The 5th generation of wireless technology is rapidly rolling around the world. It assures the jump in reliability and speed, enabling mobile devices to behave like computers connected to the wired network. But 5G networks pose some security challenges facing enterprises and consumers. Hence, it increases the need for using IoT devices.
5G access to high bandwidths will connect more users and devices. It seems like a piece of good news. But unfortunately, 5G also comes with a boon for enterprises and cybercriminals. Here are some of the prominent cyber security concerns when moving to 5G networks:
Large Attack Surface
5G networks will connect with more IoT devices, so there will be more entry points for cyberattacks. Smart devices will multiply, and each will become a potential target for hackers.
Bigger Cyber Attacks Impacts
Enterprises will depend on 5G significantly more as compared to their predecessors. For example, smart cars, air traffic, hospitals, and others rely on 5G. In addition, there are several interconnected IoT devices or infrastructures. So, a security breach in an area has cascading effects on 5G network-connected devices.
Potential for Invasive Spying
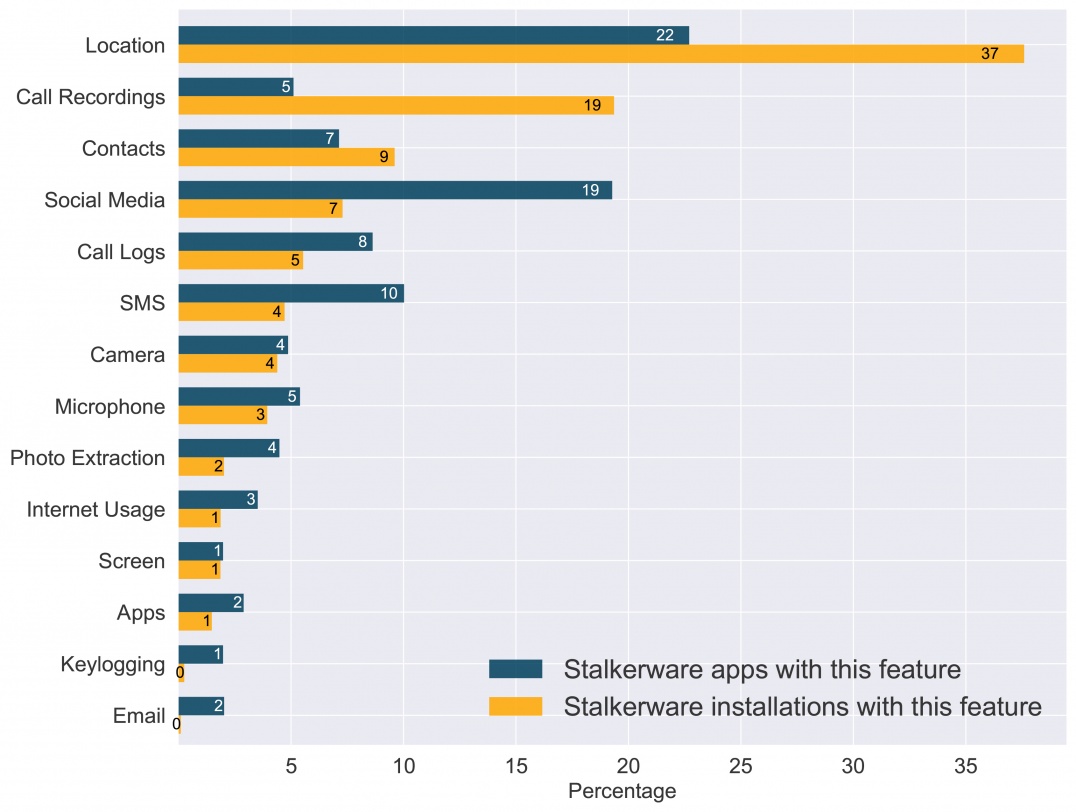
As per USA Today, manufacturers can use the enhanced connectivity of 5G devices to spy on consumers. In addition, cybercriminals can abuse the device with audio and video capabilities to listen and watch to unaware users. For example, recently, this type of risk came from government responses to the telecom company Huawei, and its 5G phone, the Mate X. Some international governments have been cautious about allowing Huawei on their networks for fear of state-sponsored spying.
Missing Security Objectives when Moving to 5G
According to Cornell University’s last year report, the 5G AKE protocol failed to meet different security goals needed by the 3GPP. AKE (Authenticated Key Exchange) is a security protocol for smartphone subscriber authentication.
Subscriber Activity Monitoring Attacks
The international researchers analyzed and found that the new security threat can exploit AKE protocols vulnerabilities. Additionally, these subscriber activity monitoring attacks utilize sham base station attacks, which cybercriminals have used while targeting security leaks in the network. Also, it targets AKE protocols and a vulnerability in the SQNs (sequence numbers) encryption.
Though 5G AKE protocols have advanced security against these fake base station attacks, the relay attacks could breach 5G’s SQN. In addition, these are more adverse than previous attacks because hackers can monitor user activity even if they have left the fake base station range.
More Threatening DDoS Attacks
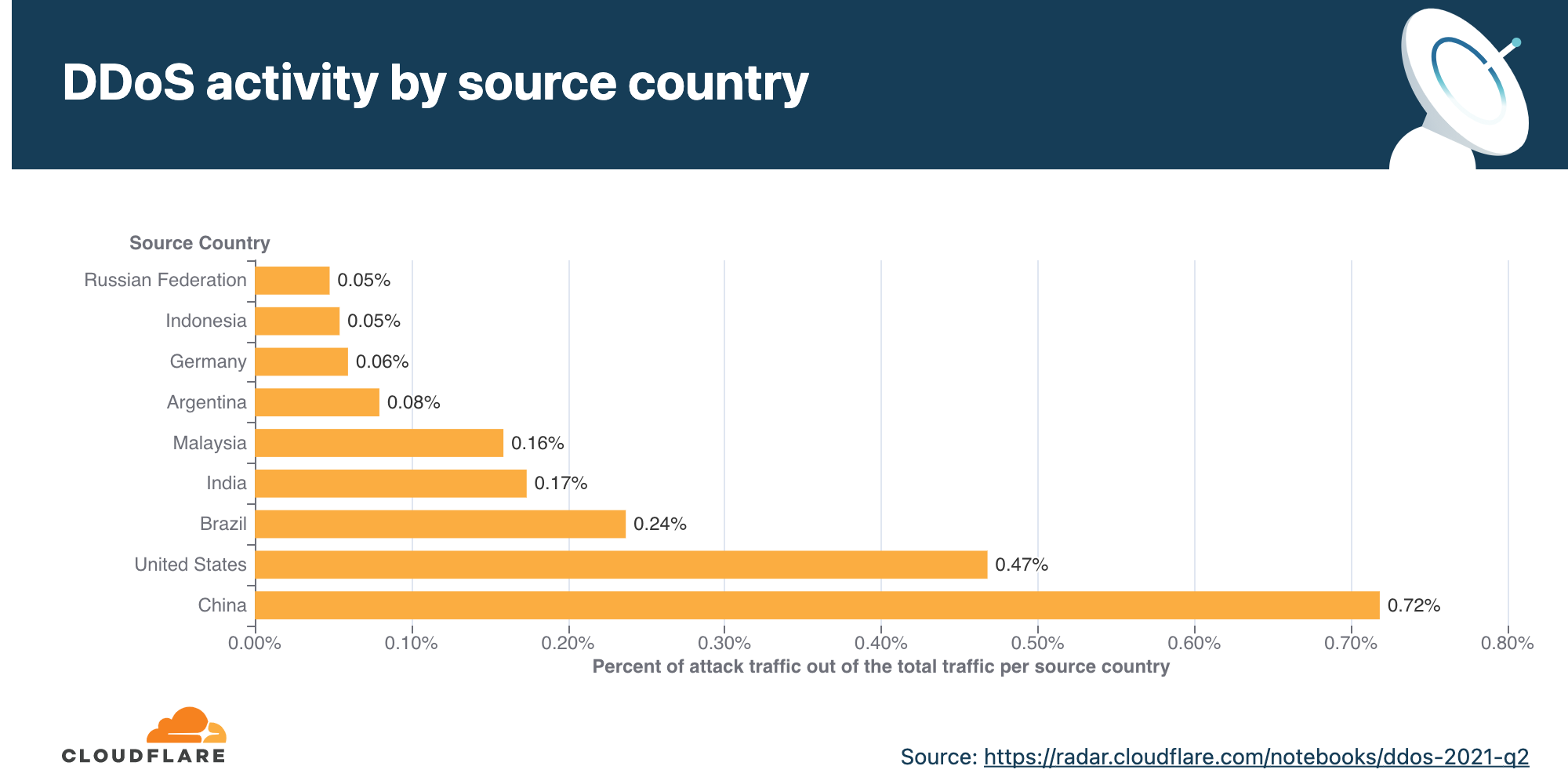
Stuart Madnick is an IT professor at the Massachusetts Institute of Technology. He said that the cyber attackers could use 5 G’s inactivity to lower the devices required to overwhelm industries in DDoS attacks.
5 G’s speed boost will make these attacks harder to handle and more efficient. DDoS attackers will strike faster in seconds, not minutes. Therefore, counter-responses to these attacks will also need to be quicker. Moreover, there will be more IoT devices for hackers to collect and harness for DDoS attacks. So, the frequency of these attacks will possibly increase.
Final Words
You can see many advancements and tech products rise from the increasing usage of the 5G network. But you need to cautiously and vigilantly approach the 5G network security needs to understand the potential 5G opens for privacy invasions. Hopefully, the next phase of moving to 5G will address these security challenges.

