
by Anika D | Sep 5, 2022 | Artificial Intelligence
Artificial Intelligence does not need any formal introduction. It is not only a buzzword; in fact, it has become an important part of your everyday life. Many companies are introducing intelligent machines for the diverse use of AI. So, it is transforming the business sectors a lot. Here you will learn about 7 types of artificial intelligence and its use.
Reactive Machines
 Source
Source
Reactive machines do not store memories; instead, they use past experiences to determine future actions. They are one of the most basic AI systems to perceive the world and respond to what it observes. They have predefined specific tasks, so they do not have any capability beyond those set tasks.
Deep Blue, a reactive machine, is IBM’s supercomputer for chess-playing. It made a breakthrough when it beat grandmaster Garry Kasparov in 1997. Deep Blue did not have any pre-applied data sets. Instead, it simply identifies the chess pieces on the board and chooses the next possible moves.
Limited Memory
Limited memory devices have the capability of reactive machines and can learn from historical data to make correct decisions. Almost all existing applications come under this type of AI. Unfortunately, these systems have short-lived memory. They can use past data for a specific period, but they can not include it in the library.
You can use this kind of technology in image recognition systems. They have thousands of pictures and labels to recognize them. When an image gets scanned by such an AI device, it uses those sets of pictures as references to understand the image contents.
Theory of Mind
The third category of AI is the theory of mind that exists only in concepts. It is also known as internal simulation, which can understand others and put itself in someone else’s shoes. It helps you to know how people’s sentiments and emotions affect their thoughts and behaviors.
One real-world example is Sophia from Hanson Robotics. It is a robot in which a camera is present in its eyes, combined with some algorithms that allow her to see. As a result, Sophia can sustain eye contact, follow faces, and recognize individuals.
Self-Aware AI
Self-aware AI deals with super-intelligent devices through their sentiments, emotions, consciousness, and beliefs. These machines are smarter than humans and can outperform them in various tasks. However, self-aware AI is still a distant reality, but companies are making efforts in this direction.
Artificial Narrow Intelligence (ANI)
This category of artificial intelligence mirrors all existing AI created to date. ANI refers to AI machines performing a specific task independently using human capabilities. These devices can do no more than their set design. Thus, they have a limited range of competencies.
These systems correspond to both reactive and limited memory AI. Even the complex AI that uses deep learning and machine learning to teach itself comes under ANI. The most common example of ANI is Apple Siri. It operates with a pre-defined set of functions. Therefore, it often has problems with operations apart from its abilities.
General AI
General AI, also known as strong AI, can learn and understand any intellectual task that a human can. It helps a machine to use skills and knowledge in different contexts. However, researchers have been unable to achieve strong AI till now. Instead, they have to determine how to make devices conscious by programming a cognitive ability set. Microsoft has invested $1 billion through OpenAI for General AI.
One of the significant attempts to achieve a strong AI is the K computer. It is one of the fastest supercomputers in the world, created by Fujitsu. It takes around 40 minutes to simulate one second of neural activity.
Artificial Super Intelligence (ASI)
Artificial Super Intelligence is a more advanced version in comparison with strong AI. It can copy the multi-faceted intelligence of humans and is better at everything. This system has a design with faster data processing and analysis, better memory, and decision-making capabilities. However, its existence is hypothetical so far.
Wrapping Up
These were 7 types of artificial intelligence and its use. Here you can see the present reality of AI and speculate on some possible future developments. In its current form, AI is a sophisticated predictive analytics engine. However, its future holds great potential.

by Anika D | Aug 31, 2022 | Emerging Technology
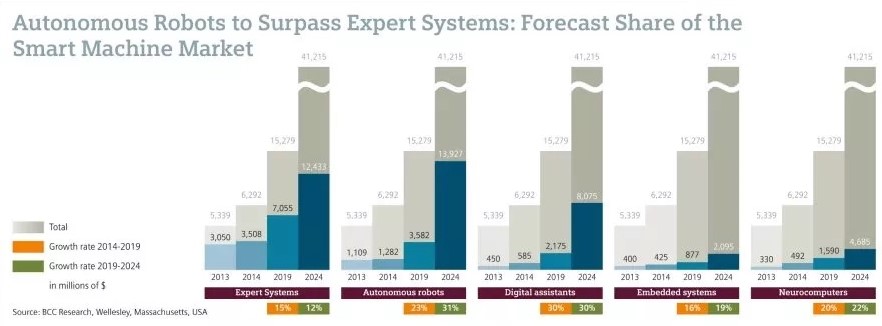
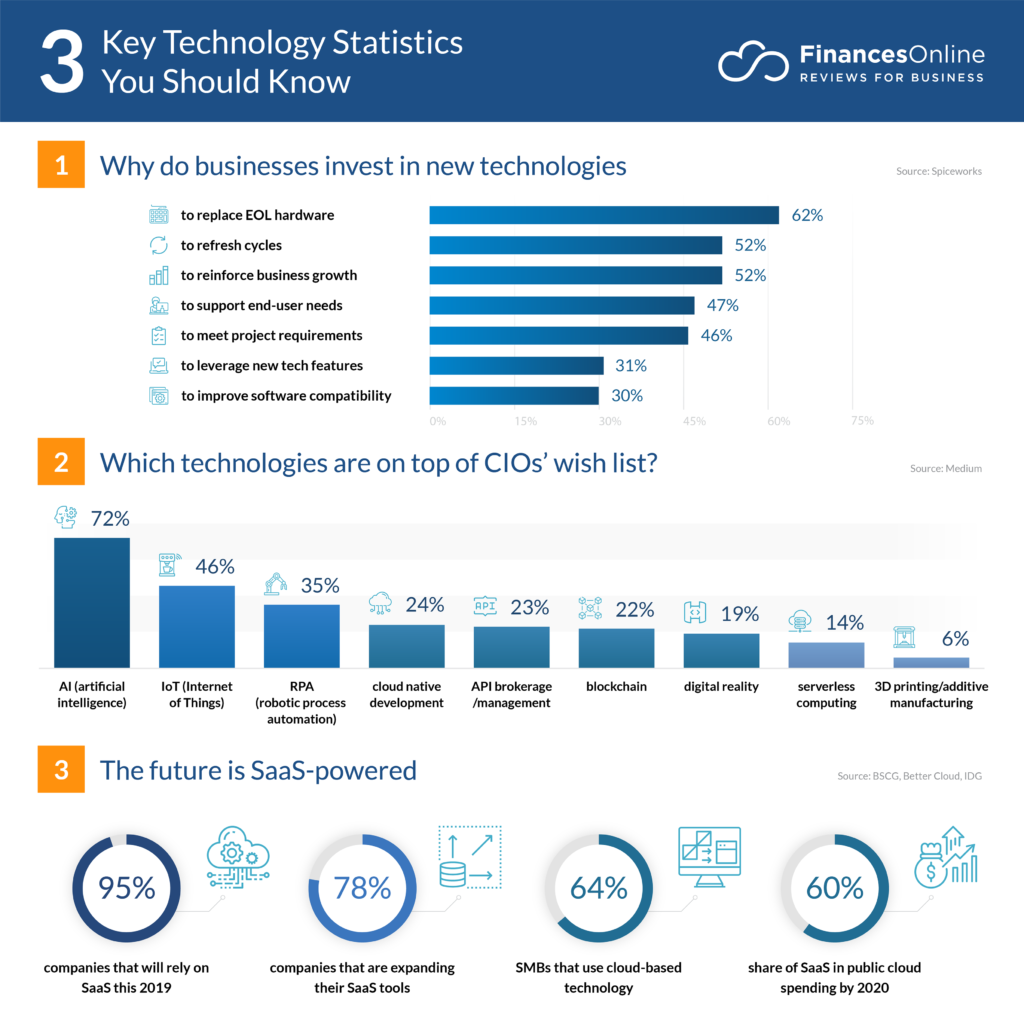
Enterprise technology trends and developments are at an all-time high and evolving daily. This amazing growth was especially witnessed after the pandemic when flexibility, security, and smart work were most needed. With the help of these robust technologies, enterprises have new opportunities and can achieve goals efficiently. So, here’s a complete list of top enterprise technology trends to watch in 2023.
Let’s have a look!
The Rise of Automation and AI
 Source
Source
Artificial intelligence and automation are at full wiggle after the pandemic. With hybrid and work-from-home cultures, businesses are looking for technology that can fulfill repetitive tasks efficiently. Thanks to AI, its chatbots, and the ability to perform simple tasks, enterprises readily use its applications.
As a result, 83% of IT leaders say AI is transforming customer engagement for the better. Moreover, robotic process automation (RPA) is one of the fantastic applications of AI. It builds software bots to carry on advanced proceedings. These automatic systems can adapt to the environment and dynamically modify their algorithms to give real-time solutions.
Use of Cybersecurity Mesh
With all the hustle of main goals, you may be making serious cybersecurity Mistakes. After COVID, cyberattacks have become frequent, and protecting your data and activity must be a priority. Cyber security mesh technology uses scalable security controls that can be transferred to various networks at different locations.
It has multiple components, like several supportive layers, such as consolidated policy management, security intelligence, and identity fabric. It aims to protect individual endpoints rather than attempting to preserve all assets with a single technology.
Rise of Web 3.0
Web 3.0 is the third generation web built using AI and the semantic web. It is powered by machine learning and artificial intelligence to give another level of experience. How will it help enterprises.? Well, it uses blockchain technology which is decentralized and completely safe. Moreover, it will allow:
- Transparent transactions and dealings of business
- Advanced security measures that will avoid breaches
- It will provide more data insight because it gives feedback in form while practicing anonymity
- It’s more affordable than other websites.
Cloud-Based Solutions
Flexibility is the new trend for enterprises, and some trending technologies are making it work successfully. Various cloud-based solutions allow employees to work from any part of the world. They can access data, stay safe and work in the most suitable environment.
The trend of hybrid and work-from-home environments is becoming quite popular. Applications like Microsoft Teams, Cisco UCM Cloud, and Webex help boost productivity and stay in touch. Many companies are turning to desktops as a service (DaaS) and virtual desktop infrastructure (VDI) to promote a flexible work culture. Some top cloud computing startups of 2022 are offering amazing cloud solutions to many firms. Moreover, these solutions are completely cloud-based, affordable, and very fast compared to others.
Use of Blockchain Other Than Money
You may have heard several times about blockchain in cryptocurrency in monetary transactions. But that is not it. Blockchain can do wonders and help enterprises to become more efficient. It uses end-to-end encryption and privacy to create incredible cyber security.
Some of its applications that will trend are:
- Tracking the location of goods
- Monitoring assets and machinery to record activity and output
- It can store a massive amount of data
- Financial accounts in record management.
After deploying blockchain technology to small business segments, you will notice how this technology can transform every sector.
Adoption of low code/no-code Development
 Source
Source
Low code, no code, also known as LCNC, will be a trendsetter technology in 2023. These platforms are specially built for noncoders by coders to do the functions of any enterprise. Luckily, it requires no knowledge of complex coding. Of course, some software developers develop the platforms, but it gives power to non-specialists to support agile operations in the enterprise.
This will reduce the costs, make nontechnical staff work on it and bring on transparency which is great. It’s becoming robust with the help of security, efficiency, and new-age technology.
Use of Modern Languages
One of the top enterprise technology trends to watch in 2023 are the use of amazing languages. These languages are relatively new but have incredible benefits for enterprises. In 2023, enterprises will bid goodbye to standard languages and welcome modern languages. It includes Rust, TypeScript, Swift, Dart, Go, Kotlin, etc.
They are trending because they use modern computer hardware and change how software is developed. For example, many large companies like Amazon and Microsoft are moving ahead with Rust. These languages are called “the most beloved language” because of their flexibility and efficiency.
Personalization Using IoB
Do you know Gartner predicts that by 2023, 40% of the world’s population will have their activities tracked digitally? Well, that’s for understanding the customer pattern. One very beneficial enterprise technology is the Internet of Behavior (IoB) which will help the organization to achieve personalization according to their customers. It will notice people’s behavior as they interact with apps and devices.
Moreover, it will bring insights into business intelligence, big data, and customer data platforms. This data records buying history, customer interactions, social media awareness, etc. Furthermore, it helps enterprises to customize their services for growth. So this will bring useful data to provide the best services in every enterprise sector.
Infrastructure as Code (IaC) Adoption
Many enterprises will use Code (IaC) infrastructure in 2023, as it is one of the most anticipated trends. It is also called software-defined infrastructure or software intelligence as code.
It allows the administration and provisioning of computer databases with the service of machine-readable definition files. Moreover, it stores IT infrastructure in software codes rather than hardware configuration tools. As a result, enterprises can check the software rather than look for each hardware.
Wrapping Up
These were the top enterprise technology trends to watch in 2023, which are the future. Gradually, all these technologies are becoming robust to transform businesses completely. Moreover, its flexibility and security make tasks easy. This immense rise was noticed after COVID when the work culture changed to digital mode. So, keep checking here for all the latest developments.
by Anika D | Aug 12, 2022 | Machine Learning
Machine Learning is all over the place; therefore, it is important to capture best practices and solutions to solve common ML problems. One of the simplest ways to catch these problems and provide answers is to design patterns.
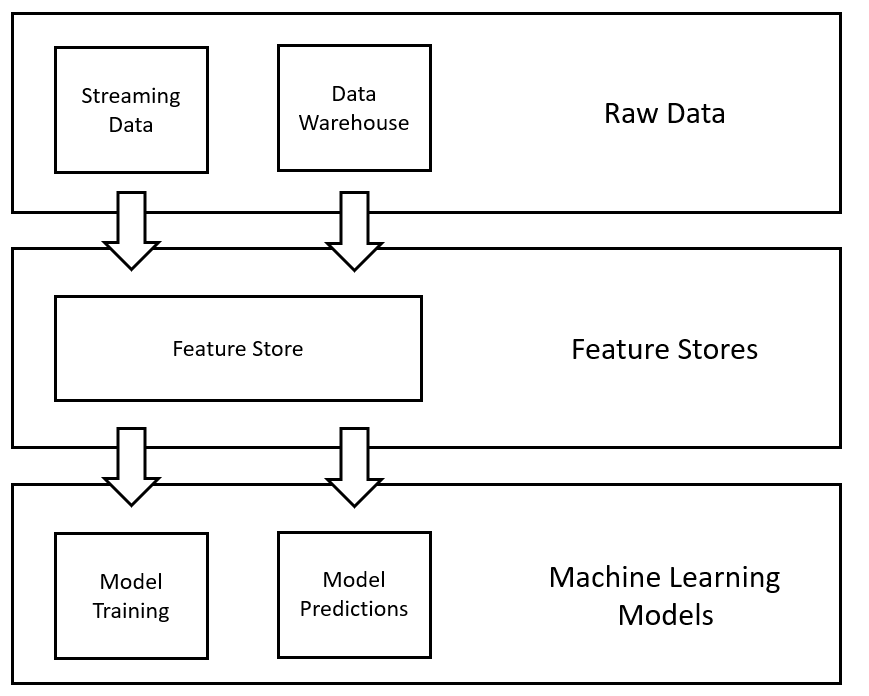
Source
“Design patterns” are the best practices used by programmers to solve common problems while designing a system or an application. Below are a few design patterns that you must try:
Problem Representation Design Pattern: Rebalancing
The common scenario in classification problems like Fraud Detection, Spam Detection, or Anomaly Detection is Imbalanced datasets. But typical Machine Learning models for such classification work by assuming that all the classes are balanced and result in poor predictive performance. Some of the common strategies to handle imbalanced datasets are as follows:
- Choose Right Performance Metric: AUC or F1 scores are efficient for performance evaluation as the goal is to maximize precision and recall.
- Sampling Methods: Resampling is widely adopted to balance the dataset classes’ samples.
- Weighted Classes: It involves penalized learning algorithms to increase the misclassification cost in the minority class.
Reproducibility Design Pattern: Transform
The idea of this reproducibility design pattern is to separate input from features. You have to extra features from raw input to train a model. But in most ML problems, you can not use input directly as feature. Instead, you must apply various transformations like scaling, standardization, encoding, and others to reproduce them at the prediction time. So, it is vital to separate the inputs from the features, encapsulate the preprocessing steps, and include them into the model to ensure reproducibility.
Model Training Design Pattern: Checkpoints
The major attributes of a scalable system are resilience and fault tolerance. The snapshot of the model’s internal state is the checkpoint. So, you can resume training from this state to another later. However, during the activity, power outages, task preemptions, OS faults, and other unforeseen errors can happen, resulting in time and resource loss.
Reproducibility Design Pattern: Workflow Pipeline
The goal of the design pattern is to isolate and containerize the individual steps of a machine learning workflow into an organized workflow. It ensures scalability and maintainability. Generally, the machine learning development workflow is generally monolithic, containing a series of tasks from data collection to model training and evaluation. But the machine learning tasks are iterative.
Tracking the small changes in the workflow during the development process becomes complicated as the process iterates many times. It introduces the concept of MLOps, similar to DevOps concepts like continuous integration and continuous delivery. The key difference between MLOps and DevOps is that it is not only the code. It is also the data that must be continuously tested and validated in MLOps.
Responsible AI Design Pattern: Explainable Predictions
Generally, machine learning models are black boxes. But it is important to clearly understand the model behavior to diagnose the errors and identify potential biases. The major factor in Responsible Artificial Intelligence is introducing explainability in machine learning. Hence, the key idea is to interpret the machine learning models to understand why and how the model made the predictions in a certain way.
Final Words
You can implement the above-mentioned techniques in most machine learning practices, but defining design patterns helps to create general reusable solutions for common problems. In addition, they help to communicate with engineers and solve problems by providing off-the-shelf solutions.

by Anika D | Aug 9, 2022 | Emerging Technology
The 5G network helps to collect a significant amount of on-road vehicle data. This information can serve various purposes, such as carrying out road maintenance, providing road weather services, and controlling self-driving cars. So, the ultimate goal is to reduce the number of road accidents.
VTT’s two-year 5G-Safe project explored various possibilities of improving road safety with 5G. Using a fast 5G network, you can collect many sensors, video and radar data. Then, you can transmit information automatically in real-time without the driver’s help. Furthermore, when processing this data via intelligent systems, you can send warnings to road users, maintenance, and third parties.
Please Slow Down near Icy Corner
One of the key applications for vehicle data collection is local road weather services. In the future, you can send real-time weather information or warnings to drivers’ satellite navigation devices. So, drivers can use this information to follow a different route while driving. In the final pilot, the 5G-Safe project showed safety and weather-related services delivered to vehicles via the 5G test network. These services included traffic safety alerts, road weather forecasts, and weather alerts.
You can transmit some automated weather warnings via the current 4G networks. However, sending real-time video footage between vehicles needs considerably more network capacity and low latency. The 5G network can support both.
Crowdsourcing Information for Road Maintenance
Source
5G emerging technology opens up new possibilities from the road maintenance perspective. This technology provides an efficient way to collect information on the road’s condition. The 5G-Safe project illustrated the usage of data to alert road maintenance providers about the range of issues that requires attention. For instance, snowy traffic signs, snow build-up on the roads, or potholes.
It is a great improvement on the current approach, where road maintenance contractors are responsible for information collection. If you can crowdsource monitoring to all road users, road maintenance contractors can work more efficiently and cut their costs. In addition, with comprehensive and reliable data, road contractors can prioritize urgent jobs.
Self-Driving Vehicles Expand their Territory
Source
Though 5G technology helps human drivers, its impact on self-driving cars can be more revolutionary. You can use real-time data to better control self-driving cars and change their behavior as per observations. VTT’s 5-G safe self-driving car Martti has already tried these possibilities.
In the final pilot, Martti drove in automated mode on the test track utilizing its warnings and sensors. MEC service gave warnings to Martti by detecting obstacles on the road in real-time. In addition, Martti received alerts of slippery roads from the weather service. Based on these warnings, the robot car could plan its route to avoid dangerous stretches.
Precise information is important in challenging conditions and expands the potential uses of self-driving cars. Currently, people use self-driving cars mostly in areas with non-problematic weather conditions. Controlling self-driving cars in the Nordic climate needs accurate real-time data. The 5G technology allows it to collect data from areas beyond the cars’ sensors.
Final Words
There is a huge interest in global services and solutions that improve road safety. So, many companies are currently planning further development of road safety solutions using 5G technology.

by Anika D | Aug 5, 2022 | Cybersecurity, Emerging Technology, Information Technology
Emails are part of every business in today’s world, but it is also one of the biggest security risks. BEC (Business Email Compromise) is rising every year. In addition, it is becoming common for criminals to use different phishing and spoofing attacks to probe organizations. In recent years, Ransomware has been growing rapidly and poses a greater risk to companies. What you don’t know is that email is a common entry place for Ransomware.
Source
But no need to worry about this. There are some countermeasures to this issue. These email security practices can go a long way for organizations from several threats. Here are some best practices to avoid Business Email Compromise:
Use Strong Passwords
It would be best to use strong passwords that meet the following criteria:
- It must complete a minimum length requirement.
- It must contain letters and numbers.
- It must contain both lowercase and uppercase letters.
- It may not have full name data.
- It should not be a commonly guessed password like 123456 or abcdef.
Use 2FA (Two-Factor Authentication)
Source
Many people think that only professionals can do 2FA, but it is not a difficult task. It is more like adding another shield to the account. Thankfully, almost every platform offers 2FA, but you can use another email provider if your system doesn’t support it. Also, if a hacker guesses your password, 2FA will stop them from entering before they get a sneak peek of your emails. Usually, two-factor authentication codes are sent to you by email, SMS, voice calls, or OTPs.
Be Careful of Suspicious Attachments
Nowadays, file sharing in the workplace mostly happens via collaboration tools like OneDrive, Dropbox, or Sharepoint. Therefore you should treat every file attachment in the mail suspiciously, even if it is from your colleague. Be more careful about the attached file with unfamiliar extensions or one that commonly delivers malware payloads (.zip, .exe, .scr, etc.).
Never Access Your Emails from Public Wi-Fi
If you take the office devices home or open your work emails from personal devices, do not access emails on public Wi-Fi. It is because cybercriminals can easily discover data passing through publicly accessible Wi-Fi. So, your sensitive data and login credentials both are at risk. Accessing emails is best when you are confident about network security. Opt for a safer option using mobile data or internet dongles outside the office.
Change Password Regularly
Many people keep passwords for years. But it is one of the biggest cybersecurity mistakes. The simplest yet most effective email security practice is regularly changing passwords. You must ensure the following things:
- Have a new email password after every 2 to 4 months.
- Use devices or do it yourself instead of leaving it to other people to update credentials.
- Do not add one of two characters to the current password when creating a new one. Change the entire password.
- Do not use passwords that you already used in the past.
Wrapping Up
BEC is a criminal phenomenon that has potentially severe consequences. BEC criminals usually live outside the country, so it is difficult for law enforcement to prosecute them. Therefore, prevention and detection are crucial. So, all companies should educate their employees and create an environment encouraging compliance.

by Anika D | Aug 2, 2022 | Artificial Intelligence, Information Technology
Have you noticed that your various accounts require multiple identity verification methods when you log in these days? You can no longer access your email, accounting system, or cloud applications by only entering your username and password. Instead, you need to enter a short code you receive on your phone or via email. Sometimes, you can also get verification calls using biometric data or a smart card.
Do you know what this is? It is multi-factor authentication (MFA). It consists of three things that you combine for identity verification. You can summarize MFA as “something you are, something you have, and something you know.” For instance, a combination of tokens, a username, password, or biometrics.
Source
Setting multiple verification methods may seem like a hassle, but it makes your accounts secure. Below are some reasons to enable MFA:
Secure Incase Passwords Get Stolen
These days password theft is evolving. Cybercriminals’ main methods to steal passwords are keylogging, phishing, and pharming. Keylogging involves secretly recording keys that strike on a keyboard. Phishing consists of fraudulent calls, emails, or SMS that ask for your sensitive information. Pharming includes installing malicious code on the device that redirects users to fraudulent sites.
Any individual or enterprise can easily become a victim of these attacks. But MFA ensures that your identity and accounts remain secure even if your password gets leaked.
MFA Adapts with Change in the Workplace
These days employees work outside the companies. So, with change in the workplace, you need more advanced MFA solutions that manage complex access requests. MFA offers multiple protection layers and evaluates potential risks while looking at the user’s location and device.
For instance, if you log in from your office, you will not get a prompt message for additional security factors. But if you log in from a café using your mobile, you will receive an SMS for verification of another factor.
Reduce the Usage of Unmanaged Devices
These days companies have embraced the remote working concept. So, employees often use personal devices or less secure internet connections. A hacker can easily install password-stealing malware on the device due to a compromised router. When you use MFA, you don’t have to worry about the security of unmanaged devices.
Improve Employee Productivity and Flexibility
Remembering so many passwords can be a huge burden. Therefore, many people use simple code, but that is easy to crack. To avoid this, many companies enforce password policies encouraging employees to set stronger passwords and update them regularly. But a new issue of forgetting the password arises with it.
Forgetting the password means password resetting, and it costs more time. In such cases, MFA allows you to sign in via a single-use code generated by an app or a fingerprint scan.
Stay Compliant
If your company deals with personally identifiable information or finances, state or federal laws may need an MFA security. MFA ensures access to protected health information by only authorized users. So, it allows your firm to remain compliant with HIPAA (the Health Insurance Portability and Accountability Act).
To Sum Up
Multi-Factor Authentication methods are quite inexpensive and easy to deploy. In addition, they provide a simple, effective solution to users and a wider business network. So, ask yourself why you haven’t already adopted this cybersecurity plan and go for it as soon as possible.














