
by Anika D | Apr 4, 2022 | Cybersecurity, General
Cyber attacks are the new age ” war” as the data is crucial. Whether you’re a common person, a startup, a bank, or any organization, you can always welcome attacks. In this new age era, everyone stores all the valuable information on the Cloud. The exchange of every detail is with the help of the internet; it’s crucial to protect it more than ever. So, to avoid all this; keep reading to know seven serious cybersecurity mistakes you’re probably making.
#1 Using a Single Password for all the Accounts
Source
It is probably the most common and ignored mistake people make. If you’re using a strong password for all the important accounts, all your accounts are at risk if one of them is compromised. In 2020 identity theft was up by 42%, compared to 2019. So, use different and strong passwords for all the crucial accounts.
#2 Skipping Updates
Skipping authorized necessary software updates on phones and laptops can prove dangerous. As US banks are getting ready for attacks from Russian hackers, the professionals have advised individuals to be alert too. If you’re not updating software regularly, your system becomes vulnerable and easy for breaching. So, update it timely.
#3 You Always Click on “Agree”
It’s obvious as one can’t read and go through everything and then click on “I Agree” on internet pages. But, it can be very dangerous and bring malicious viruses to your account. So, before clicking “I agree” next time, type:
- On a Windows PC, press Control + F.
- On a Mac, press Command + F.
Now, type in terms like “third party,” “GPS,” “tracking,” and “data.” You will find out if there is any data permission. With the US becoming a 6G power, it will welcome some great attacks, and you must take steps with alertness.
#4 Using Unprotected wifi
Using unprotected wifi to work on crucial information is dangerous. For example, suppose you’ve started a venture, and your startup needs a website. While accessing the website, you’re on public wifi. Hackers can easily decode your location with data and ruin your website. So, avoid using public wifi or using VPNs while doing it.
#5 Not Keeping Track of all Online Accounts
Source
Cybercrime is Up by 600% after COVID 19, and at this rate, you can’t think that you’re safe. So, keep track of all your social media accounts as they have your contact details, payment info, and other valuable data. So, having old unused accounts means someone can hack the information. So, take some time, track them all, and delete the unused ones.
#6 Don’t let every App run Your System
The computers and phones come with loads of pre-installed apps. You may never check them, thinking they are safe, and you can’t delete them. But, this puts your information at risk. Many professional hackers can attack these apps to attack your system. So, keep checking and delete them timely.
#7 Depending Solely on Antivirus
Businesses suffered 50% more cyberattack attempts per Week in 2021, and you may think that antivirus is enough. Well, it is not. It would help if you had a firewall, third-party solutions, and staff training. Also, your home computers must have robust firewalls.

by Anika D | Feb 24, 2022 | General
New research is using quantum computing and machine learning to find out what’s inside a black hole.
Scientists are doing new research by leveraging the application of artificial intelligence and quantum computing to find out what’s inside the black hole. The study could help understand the holographic duality, a mathematical conjecture, connecting theories of particles and gravity.
The black hole wraps space-time because of its surprisingly huge mass. As a result, its gravity exists and connects to the particles lying above it. Please note that the black hole exists in three dimensions while particles exist in two dimensions. As a result, the hole exists in the three-dimensional space and projects through particles.
Many scientists say that the universe is a holographic projection of particles, which leads to a consistent quantum theory of gravity.
What Do Theories Say?
- Einstein claimed that there are no particles in the universe. There is just space-time.
- According to the Standard Model of particle physics, the universe has no gravity but just particles.
- A study published in PRX Quantum examines probing holographic duality using deep learning and quantum computing. The purpose of the study was to find the lowest energy state of quantum matrix models.
Quantum matrix models represent the particle theory. Holographic duality suggests everything in a system that represents particle theory affects the system that represents gravity. As a result, it solves a complex quantum matrix model that could provide more information about gravity.
What are Quantum Matrix Models?

Think of numbers in the models as sand grains. The matrix model is in the ground state when the sand is level. In case of ripple in the sand, you need a way to level them out. To solve this problem, scientists first considered quantum circuits represented by wires. Each qubit (short for a bit of quantum information) is a wire. Gates exist on the top of wires, and they represent quantum dictating how information passes along the wires.
Because Quantum matrices are one possible representation of a black hole, arranging them can help us know what the black hole looks like inside.
Final Words
Existing quantum hardware is not enough. They can handle only a few dozens of qubits. It is also very expensive for further research. So, in order to fully explore and discover what’s inside the black hole, more research and advanced hardware are needed. Nevertheless, the study can reveal a lot of surprising things about our universe.

by Anika D | Feb 18, 2022 | Business, General
The risk assessment is a systematic process to identify, analyze and evaluate risks at the workplace and decide the control measures. The control measures make sure to remove or reduce the risks of loss, injury or damage in the workplace. Legally, it is necessary for all companies to perform risk assessments. If an organization has more than five employees, it is important to prepare a written record.
The organization’s ability to remove or control risks rely on its expertise to anticipate dangers. Risk assessment is a dynamic and proactive process that prepares organizations for any kind of danger in advance. If you are wondering how to complete the risk assessment process, go through the steps listed below:
Step 1: Recognize the Hazards
If you want to identify hazards, it would be best to understand the basic difference between risks and hazards. A hazard is a source of potential harm whereas a risk is a probability of a person getting harmed. You can identify hazards by using different techniques like inspecting the workplace or taking employee feedback.
Step 2: Identify the Harm with Hazards
Source
When you identify the potential hazards like heat hazards, chemical reactions and more, determine who will be affected the most. Also, determine the degree or kind of damage one will suffer. It helps you to set priorities and look for optimal solutions related to different risks.
Besides the extent of possible damages, make sure to take into account the vulnerability of employees in different workplaces. Moreover, do not forget to consider pregnant ladies and disabled people.
Step 3: Evaluate the Potential Risks and Decide the Control Measures
Once you gather the list of potential harms, examine how likely that danger will appear. Also, consider the seriousness of the consequences. These risk estimations will allow you to find where you should minimize the risk level and what are the potential dangers. It is better to create a risk assessment chart for smooth learning.
Step 4: Record All Findings and Implement Them
It would be best if you create a proper record of all the risk assessments. It can help the organization to maintain track of risks, hazards and effective control measures. Proper documentation means a detailed description of processes in risk assessment, detailed explanations on the conclusions, proper draft of evaluations.
You can use a risk assessment template to record your findings. Then, share the proper risk assessment report and key findings with the department who can implement the necessary changes.
Step 5: Review the Risk Assessment Report
Source
If there are any significant changes in the workplace, it is necessary to re-evaluate the risk assessment and update them. Sometimes employees notice a new issue, improvements, or any accidents that occurred after the implementation of changes. Moreover, all these factors must be updated and re-evaluated for designing proper control measures.
Conclusion
A risk assessment is important to create a safe workplace and prevent accidents. So, awareness of potential hazards is a must. It is a team responsibility that needs proper participation of upper management, employees, front-line management, and industrial hygienists.
By putting proper time and effort into these safety initiatives, you can make a good investment. Also, when employees are safe then only productivity can be improved.

by Anika D | Feb 12, 2022 | Cybersecurity, General
On Saturday, Microsoft warns Ukraine of destructive malware in their government and private systems. It was revealed as the Russian troops were massed at the borders of Ukraine and many government agencies had their websites defaced.
It is possible that the malware can copy and leak confidential information from the government systems in Ukraine. The mastermind behind the malware is not clear, but agencies point fingers towards Russia for this cyberattack. The reason for this is the tension across the Ukraine-Russia border these days.
According to New York Times, the code appear and deploy shortly after talks stalled among Russian diplomats, the U.S., and NATO. Further, Microsoft claims that the code looks similar to ransomware and designed to render targeted devices inoperable.
What is the Solution to Malware Detected on Ukraine Systems?

Source
Microsoft stated that all companies should investigate to know the origin of the malware. Also, every company should implement the defense through malware to protect data.
A Ukrainian security official told Reuters that the government believes the hackers are connected to Russia. They further stated that Russia’s intelligence services carried out the cyberattack on government websites in Ukraine. But, Moscow denied the involvement in cyberattacks against Ukraine.
How to Protect the System from Cyberattack?
According to Verizon’s 2019 Data Breach Report, about 28% of data breaches are connected to malware. It threatens every organization and is becoming more common every day. Countries and companies should both work hard to prevent their data from destructive malware.
Further, there is no solution to cyberattacks, but you can detect the malware and protect your system with smart moves. Here are some tips for you to save your computers or laptops from cyberattacks.
- Always choose a strong password for your private and confidential data files.
- Try to include at least eight characters with an uppercase letter, a lowercase letter, a number, and a symbol in the password.
- Enable multi-factor authentication on your system, such as a PIN or security questions in addition to a password.
- Do not save the password on your browser or your system. It is better to remember the password in mind.
Keep in mind that no software is completely safe against malware. But the software vendors regularly update their products to make them more defensive against viruses or cyberattacks. Install and update anti-virus software on your system to protect them from potentially destructive malware. Also, never share your password with anyone.
Conclusion
Malware infections can be devastating for organizations. By interrupting critical workflows and stealing or encrypting crucial data, it can cause serious financial and reputation damage. Protect yourself and your business from cyberattacks with effective cybersecurity. Also, perform regular backups to offline storage and keep changing your passwords to make sure your system is free from viruses.

by Anika D | Feb 9, 2022 | Blockchain, Emerging Technology, General
Nowadays, Blockchain is a trending disruptive technology. It is due to the close connection of this technology with the cryptocurrency industry. This put a direct impact on the financial trends of organizations.
Blockchain disruption is one of the major shifts this year. People from all walks of life are getting involved either in buying cryptocurrency or supporting projects like Ethereum, NEO, Bitcoin, and others. Further, a record five social network giants are defending against the disruption of blockchain.
Scroll down to get a broader idea of how these networks are transforming their businesses with blockchain technology.
Twitter
Twitter is America’s third-largest social network. It is the platform where Elon Musk shamelessly pumps crypto coins. In 2021, there were 220 million tweets about NFTs, and in January 2022 alone, there were 60 million more tweets for the same. In November, crypto to-obsessed CEO Jack Dorsey left, but Twitter is still focusing on a decentralized future. It is focusing more on creative tools, tipping other tweeters with Bitcoin, and allowing them to display their NFT collections.
Platforms: Bitcoin, Ethereum
Tencent – Cloud Blockchain
More than a billion people use Tencent, which is one of the largest networks for gaming, messaging, and shopping. Now, the company is developing a unique platform known as Tencent Cloud Blockchain. Some provinces like Hainan, Guangdong, and Beijing, use this platform to issue e-invoices for healthcare and transportation. As of last year, Tencent processed more than 15 million transactions.
Platforms: ChainMaker, Hyperledger Fabric
Facebook – Metaverse
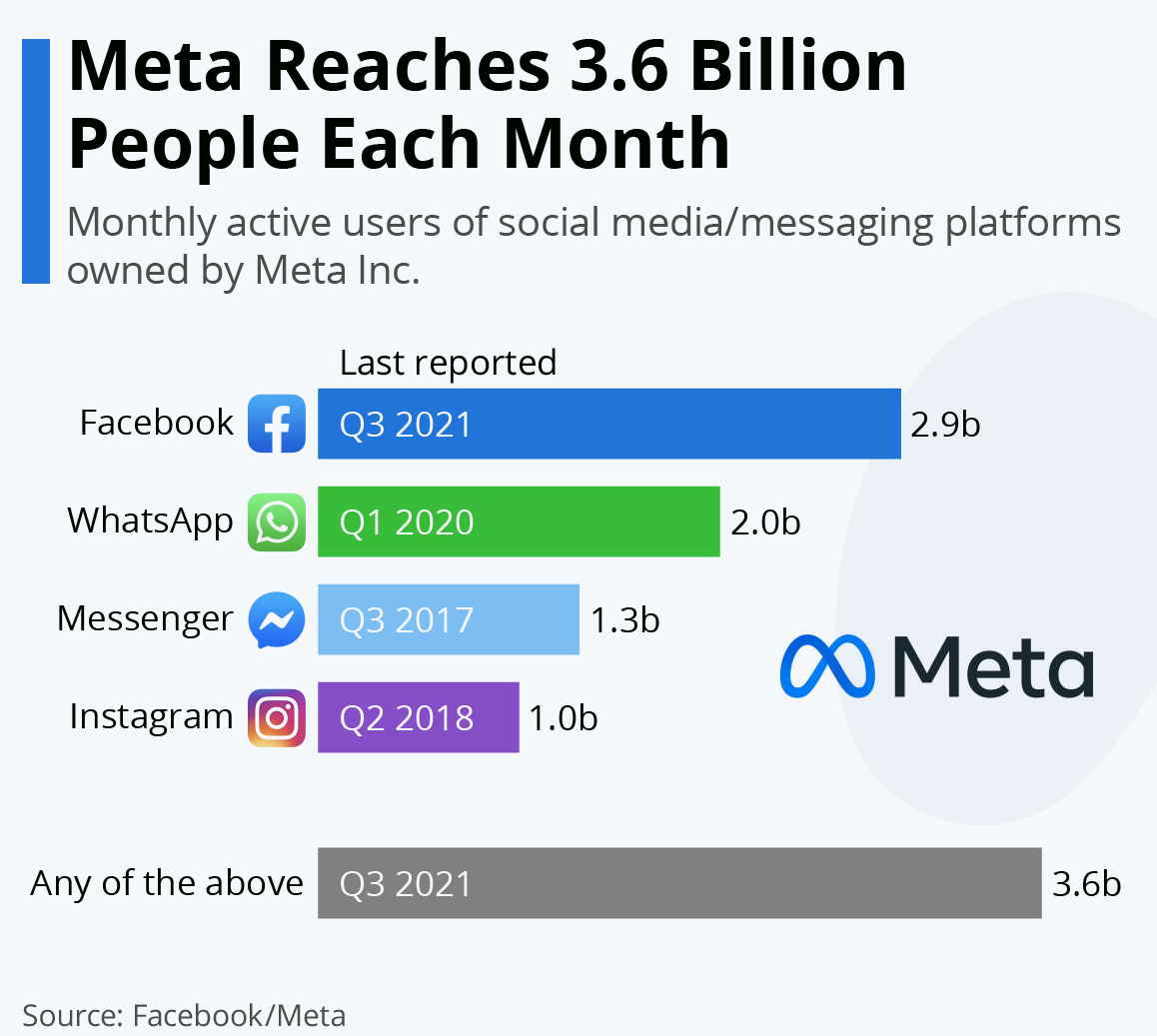
Source
Facebook decides to rebrand itself as Meta and jump into the theoretical Metaverse could be a boon for blockchain. After all, a comprehensive virtual world is a true environment for cryptocurrencies, NFTs, digital wallets, and more. Metaverse is a much-hyped cryptocurrency, and hope that Facebook’s big push into metaverse can bring more success for it.
Blockchain platforms: Diem
LINE Corporation
It is Japan’s largest messaging app and has more than 300 million users. The company has developed a proprietary blockchain, also called LINE, which is owned by Softbank Group and NAVER Corporation. The services include a cryptocurrency exchange, NFT market, and digital wallet. At the end of January 2022, the market cap of LINE was $655 million.
Blockchain platform: LINE Blockchain
Kakao Company – KraafterSpace
Kakao is South Korea’s dominant messaging app that has nearly 52 million users in the country. It also has a marketplace for trading NFTs, which is known as KraafterSpace. Here users can purchase token artwork directly through Kakao’s messaging app. Last year, Kakao launched a $515 million Klaytn growth fund to support developers willing to contribute to its blockchain system.
Platform: Klaytn
Final Words
Organizations and social networks believe in cryptocurrency and constructing their platforms. Also, women investing in cryptocurrency due to which networks like Twitter, LINE, and more are developing their blockchain platform and supporting the disruption.

by Anika D | Jan 31, 2022 | Business, Emerging Technology
Whether you’re starting your monumental project or a startup, the constant question is, do I need a website? So, the answer is yes. Over the years, consumer behavior has changed, and 81% of shoppers conduct online investigations before purchasing. If you still feel unconvinced, then keep reading to know the significance of a website in your startup. Let’s have a look.
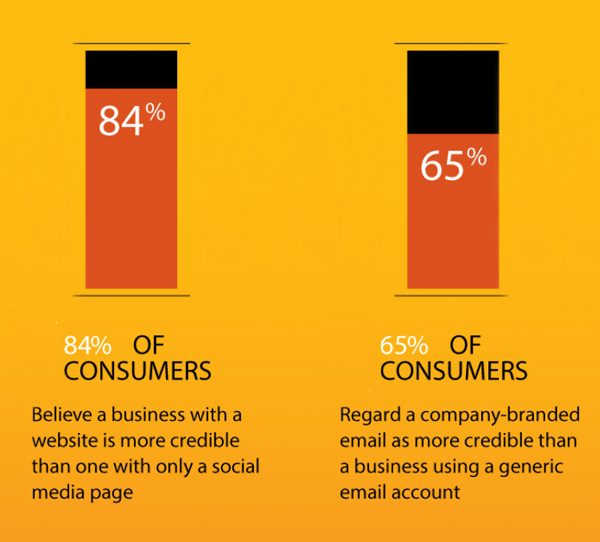
Source
A website is More Credible
A well-put website shows your customer that you’re trustworthy. It becomes more vital for a startup as any customer will search you on Google after checking you on any other platforms.
Most customers drop the idea of engaging if the startup doesn’t have an official website. So, startups are involved in leading software development and engineering trends to create competitive and user-friendly websites.
Creates a Brand Name
A website creates a brand name with a unique logo, domain name, and virtual presence. It protects you against identity theft. Getting a notable name after an entire establishment is challenging and may involve many legal issues.
Boost you up in SEO Rankings
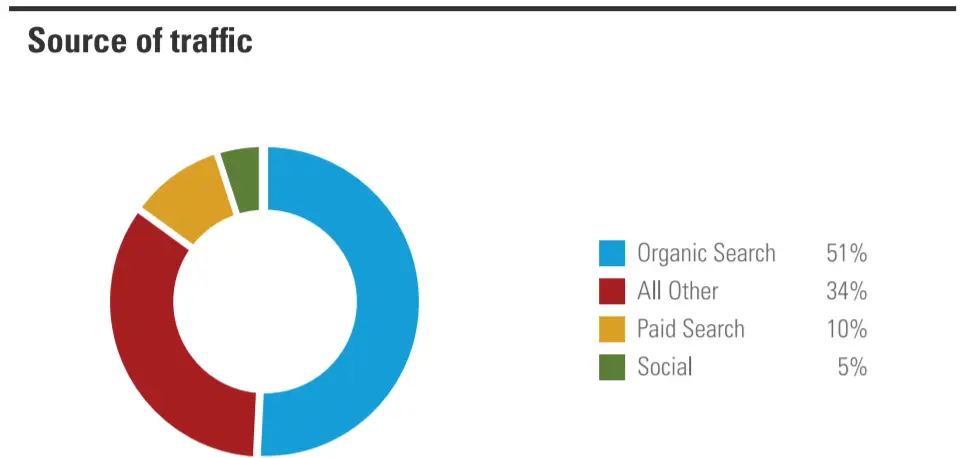
Source
Marketing and publicity are crucial for any startup, and you can up-level your search engine rankings with a website. A website that is SEO optimized is necessary for higher Google rankings and organic traffic.
It helps you reach your target and larger audience. Especially business storytelling through engaging UX design, quality content, font styles, descriptions will improve your sriracha engine rankings. This is the first towards creating a virtual space among so many competing websites.
Marketing
A 24*7 available websites are a sales platform for your startup. You can’t operate social media phone calls over time. But, a website is available around the clock. It has all the information a customer needs, with a safe payment gateway. So, designing a website with simple navigation and cyber resiliency is a great way to market your idea.
You can Have an Eye on Your Competition
A website is also vital for evaluating competitors. You can study the strategies of leading sites and what they offer. This makes your endeavor digitally updated and helps alter plans in any segment.
Cost-Effective Solution for Startup
This is the best solution for providing a platform for your startup. 63% of shopping begins online, so creating a website is like launching yourself digitally. The expense of creating pamphlets and hiring multiple teams is very extensive.
On the other hand, a simple, optimized, secure website is budget-friendly and does not require professional knowledge. Of Course, after reaching some goals, you can make it unbeatable with the help of professionals.
Let’s Wrap it
Now, you can answer the question, if I need a website? Ofcourse, it is vital for an official presence, trust, marketing, and staying up to date. But, apart from this, it’s easy to create and very affordable for a startup. So, make your endeavor digitally strong and stay updated with full proof, competitive and attractive websites.















