
by Anika D | Apr 8, 2022 | Emerging Technology, General, Information Technology
The nature of your work and different factors influencing workplace safety have developed rapidly in the last couple of years. Moreover, people responsible for preventing injuries and managing the wellness of employees adopt new strategies and a holistic approach. Many major companies are leading the drive toward a hybrid-work future.
Source
An effective safety program in the hybrid future offers simultaneous support for a workforce between different work environments and multiple locations. Similarly, safety plans must account for an ageing workforce and the rising mental health challenges and stress levels affecting worker morale. Here is a list of workplace safety trends in the future:
Employee Wellness
The hectic schedule of everyday life contributes a lot to the rise in depression and anxiety. Employee’s health care calls have increased with the growing mental illness and work stress awareness. In addition, the worldwide pandemic crisis magnified the requirement for employee safety and wellness initiatives. Many people struggle to create boundaries and avoid burnout while working from home and juggling multiple responsibilities.
Workplace safety wellness trends are more vital than ever. As a result, employees will be more likely to prioritize self-care in the future and invest in programs that spotlight wellness. With work shifts towards remote and hybrid models, the wellness program’s nature will also change. However, companies may provide credits towards home equipment and gym memberships with catered healthy lunches and workout rooms.
Flexible Work Timings
Source
A sudden mass movement to remote work gave many employees the relaxation to pick a working schedule. Since employees do not have to work during regular office hours, they can carve out timings suitable to them. For example, early morning risers and night owls can work during timings they feel most focussed with fewer distractions. This freedom allowed professionals to be more productive and handle other responsibilities.
AI-Augmented Workforce
As per the world economic forum predictions, there will be 97 million new jobs by 2025 due to AI. However, people will also find role changes in their existing jobs, and they will increasingly augment their capabilities using AI. Initially, AI will help to automate repetitive elements in day-to-day jobs and allow employees to focus on fields that need imagination, creativity, and emotional intelligence.
For instance, lawyers will use AI to cut down the time spent in reviewing cases. In contrast, doctors will diagnose a patient’s illness with computer vision capabilities. In retail, store managers can plan inventory with augmented analytics and sales assistants can predict what shoppers are looking for.
Incident Management Documentation
It would be best to emphasize finding and eliminating hazards before any issue arises. So, everyone in the business needs to report the incidents properly and show that there is any need for additional safety measures.
However, all companies do not have consistent and clear incident management procedures. So, finding a partner for straightforward and easy-to-use documentation will make employees’ work easy. After all, you may never know when an incident occurs, and you may have to make the official report.
Conclusion
After various challenging years for employees and the global economy, 2022 holds scope for great growth. As the hybrid human resource becomes a norm, employee health and safety get closely linked to the workforce. Moreover, the concept of safety and wellness will spur the innovation of technology solutions in the future.

by Anika D | Apr 4, 2022 | Cybersecurity, General
Cyber attacks are the new age ” war” as the data is crucial. Whether you’re a common person, a startup, a bank, or any organization, you can always welcome attacks. In this new age era, everyone stores all the valuable information on the Cloud. The exchange of every detail is with the help of the internet; it’s crucial to protect it more than ever. So, to avoid all this; keep reading to know seven serious cybersecurity mistakes you’re probably making.
#1 Using a Single Password for all the Accounts
Source
It is probably the most common and ignored mistake people make. If you’re using a strong password for all the important accounts, all your accounts are at risk if one of them is compromised. In 2020 identity theft was up by 42%, compared to 2019. So, use different and strong passwords for all the crucial accounts.
#2 Skipping Updates
Skipping authorized necessary software updates on phones and laptops can prove dangerous. As US banks are getting ready for attacks from Russian hackers, the professionals have advised individuals to be alert too. If you’re not updating software regularly, your system becomes vulnerable and easy for breaching. So, update it timely.
#3 You Always Click on “Agree”
It’s obvious as one can’t read and go through everything and then click on “I Agree” on internet pages. But, it can be very dangerous and bring malicious viruses to your account. So, before clicking “I agree” next time, type:
- On a Windows PC, press Control + F.
- On a Mac, press Command + F.
Now, type in terms like “third party,” “GPS,” “tracking,” and “data.” You will find out if there is any data permission. With the US becoming a 6G power, it will welcome some great attacks, and you must take steps with alertness.
#4 Using Unprotected wifi
Using unprotected wifi to work on crucial information is dangerous. For example, suppose you’ve started a venture, and your startup needs a website. While accessing the website, you’re on public wifi. Hackers can easily decode your location with data and ruin your website. So, avoid using public wifi or using VPNs while doing it.
#5 Not Keeping Track of all Online Accounts
Source
Cybercrime is Up by 600% after COVID 19, and at this rate, you can’t think that you’re safe. So, keep track of all your social media accounts as they have your contact details, payment info, and other valuable data. So, having old unused accounts means someone can hack the information. So, take some time, track them all, and delete the unused ones.
#6 Don’t let every App run Your System
The computers and phones come with loads of pre-installed apps. You may never check them, thinking they are safe, and you can’t delete them. But, this puts your information at risk. Many professional hackers can attack these apps to attack your system. So, keep checking and delete them timely.
#7 Depending Solely on Antivirus
Businesses suffered 50% more cyberattack attempts per Week in 2021, and you may think that antivirus is enough. Well, it is not. It would help if you had a firewall, third-party solutions, and staff training. Also, your home computers must have robust firewalls.
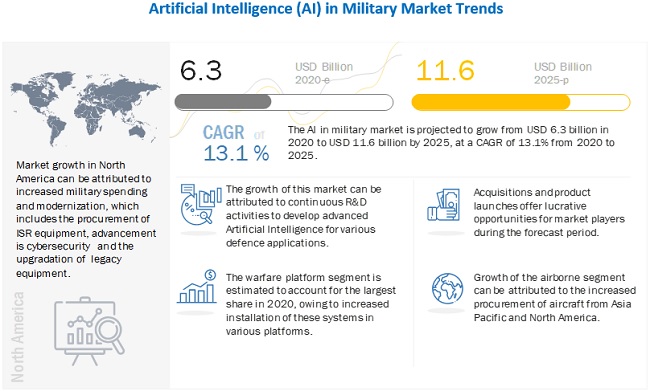
by Anika D | Mar 7, 2022 | Blockchain, Cybersecurity, Emerging Technology, Industrial IoT
The worldwide military apparatus undergoes significant transformation to strengthen capabilities. Some of the latest technologies like Artificial Intelligence, Robotics, and the Internet of Things optimize military efficiency and defense operations. Nowadays, hybrid approaches replace traditional warfare. The latest technology trends are transforming battlefields in the aspects like lethality, connectivity, sustainability, and autonomy.
Connectivity solutions mark concerns like how to communicate or direct operations. In addition, advances in weapons and missiles improve lethality, making effective battlefield operations. In the case of autonomy, companies utilize AI and robotics to execute strategies without human interference. Finally, startups are increasing sustainability with technologies including electrification and additive manufacturing.
Some of the emerging technologies that advance the defense field are listed below:
Artificial Intelligence

Source
The usage of AI in the army boosts computational military reasoning for ISR (intelligence, surveillance, and reconnaissance) missions. It empowers autonomous weapon systems and enables equipment safety management resulting in minimum casualties. By controlling machine learning and digital twin technology, defense manufacturers check new military product iterations and allow predictive military assets maintenance.
Advanced Military Equipment
Defense is making more advanced and sophisticated defense equipment to counter increasing threats. Innovations starting from space militarization to directed energy weapons are underway. Moreover, the defense industry is placing its goal to achieve net-zero emissions.
For example, it invests in electrification methods by using electric propulsions in military aircraft and testing hydrogen fuels. In addition, many companies are advancing research in nanotechnology and biotechnology for creating equipment like self-healing armors, etc.
Internet of Things (IoT)
Applications of IoT in the army include connecting planes, ships, drones, soldiers, tanks, and operating bases in the cohesive network. It enhances perception, response time, and situational awareness. AI, 5G, and Edge computing support the smooth data flow across all military branches, strengthening the control and command structure.
Big Data Analytics
The warfare future depends on information and the ability to extract in-depth knowledge. Army with the capabilities to pull out the critical data quickly and accurately and then securely spread the information will have an advantage. Big data analytics decipher insights from the various sources to do that.
Cyber Wars
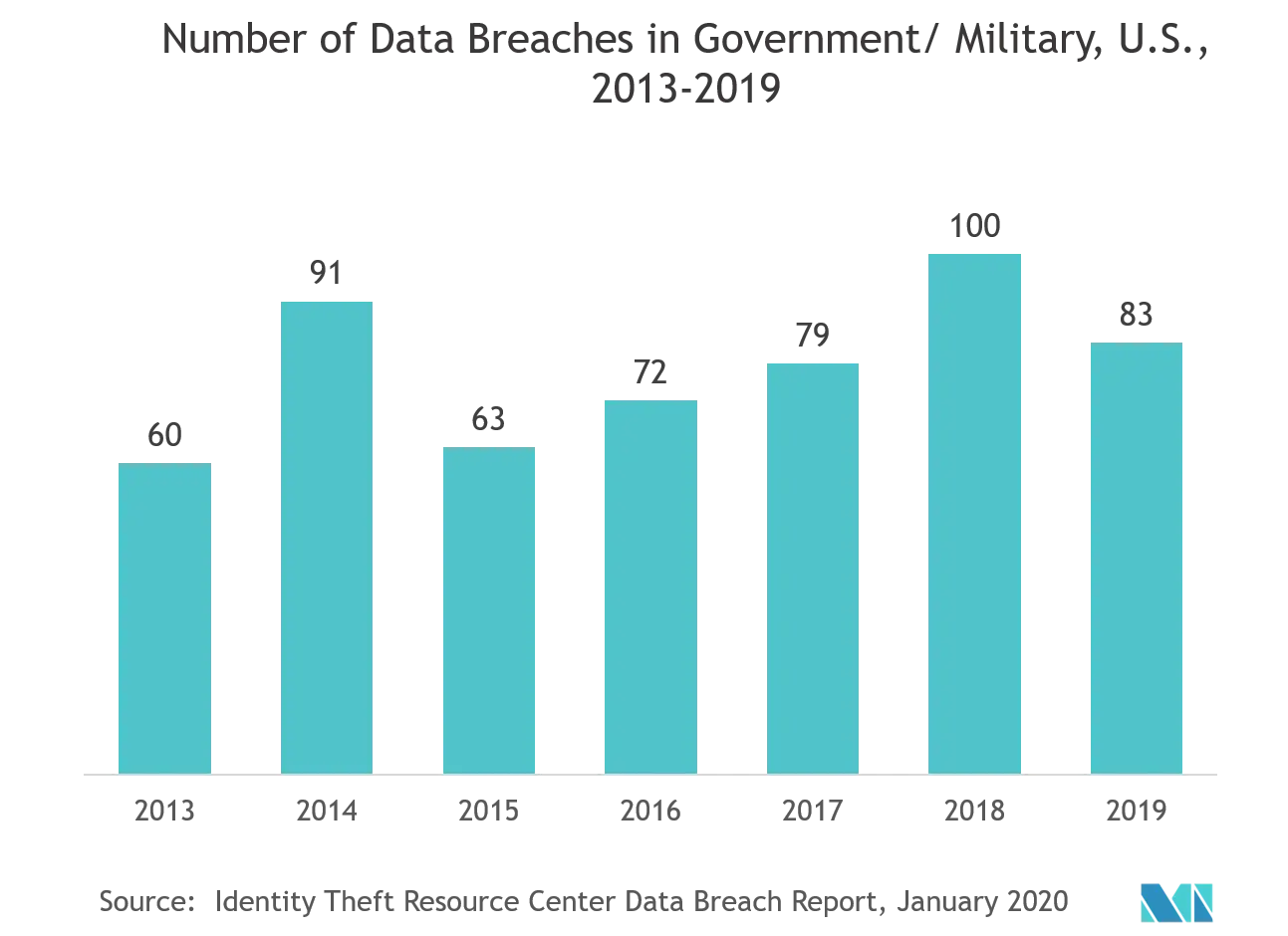
Source
Military systems are most vulnerable to cyber-attacks that potentially lead to classified military information loss and army systems damage. Over the last ten years, the severity and frequency of cyberattacks have increased.
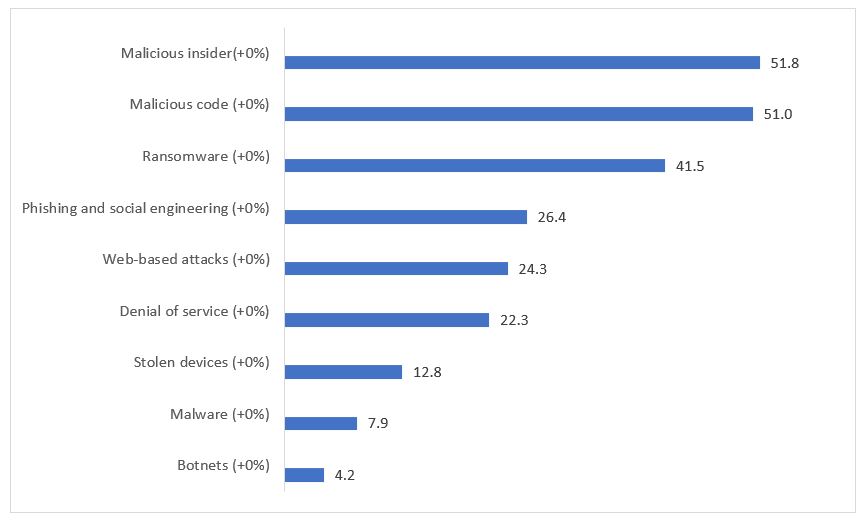
As a result, related army equipment security for significant institutions and nuclear security are substantial areas to deal with. In addition, militaries are developing aggressive cyber warfare capabilities, from ransomware and malware to phishing attacks.
Blockchain
Blockchain offers information security while sharing relevant data with the concerned parties. Therefore, defense startups create blockchain-based solutions to save confidential military data and prevent cyber threats. Its other applications in the defense industry include procurement process streamlining, supply chain security, and device tracking.
Final Thoughts
Understanding that the war landscape changes exponentially with new technologies is essential. For example, intelligent systems, lethal autonomous weapons, and AI are significant drivers for offensive and defensive army capabilities. Therefore, companies make dual-use technologies and military modernization solutions for civilian and military benefits.

by Anika D | Mar 3, 2022 | Cybersecurity, Information Technology
The western nations imposed several severe sanctions on Russia after it invaded Ukraine. As a result, banks are ready as they’re predicting revenge in the form of cyberattacks or cybercrimes. So, let’s discover all the buzz around this news.
So, What’s the News?
Last Saturday, the scenario between Russia and the West became very intense. The United States and its allies blocked Russian central banks from the SWIFT international payment system. Also, they moved the decision to place restrictions on the Russian Central Banks reserves.
Source
Western countries and the United States were already aware of the tension increasing between Ukraine and Russia. So, cyber security was taking all measures to stop cyber crimes from Russia and its supporting nations. As a record, 58% of cyberattacks from nation-states originated in Russia, according to Microsoft. So, the response is quite apparent.
A Serious Threat to Banks – Cyberattack ?
Earlier Microsoft warned of a destructive cyberattack on Ukrainian computer networks, and soon after, the attack on Ukraine began. So, with all the western countries opposing Russia’s moves. So, what kind of cybercrime can western countries face as a retaliation?
So, all the activities going on for a few months and its response has made the Global Banks a target for a cyber breach. They have begun with robust cyber security staff, training, advance monitoring, and clearing all bugs for any data leaks. Banks are especially preparing for ransomware, malware, DoS attacks, theft, and data wiping.
Various popular banks like Citigroup Inc (C.N), Morgan Stanley (MS.N), JPMorgan Chase & Co (JPM.N), Goldman Sachs Group Inc (GS.N), Bank of America Corp (BAC.N) have refused to share their course of action for dealing with any potential threat.
Even though banks have a robust cybersecurity plan, they are on alert for dealing with any attack. But unfortunately, a minor carelessness can cost too much.
Response of Famous Personalities
Some of the influential personalities presented their say on the matter. Already cybercrime is 600% up after COVID, and such robust growth of attacks is a little problematic. So what did some famous people say:
According to Valerie Abend, who leads Accenture’s global financial services security group, “Banks are incredibly prepared. They have taken out their playbooks, and it’s practice, practice, practice.”
Source
Swarthmore Group’s senior manager of fixed income portfolio, Steven Schweitzer, said there would be some revengeful measures by Ukraine and its allies. However, the least costly thing is some cyber-attacks.
The global head of intelligence at the Financial Services Information Sharing and Analysis Center, Teresa Walsh, expressed her views too. She said it wouldn’t be wise not to prepare for some retaliation. The Ukraine and allies have been giving signals in general issues for now. She asked everyone to be cautious of cybercrimes. Walsh also said that the preparation must begin now and that no one should wait for the crises.
Bottom Line
So, with all the buzz going around for months, western countries are protecting their valuable data at all costs from cyberattacks. Although banks are powered with strong cybersecurity, some careless glitches can still cost a lot. Also, It has been advised to write an effective cyber security strategy action plan for private businesses too.

by Anika D | Feb 12, 2022 | Cybersecurity, General
On Saturday, Microsoft warns Ukraine of destructive malware in their government and private systems. It was revealed as the Russian troops were massed at the borders of Ukraine and many government agencies had their websites defaced.
It is possible that the malware can copy and leak confidential information from the government systems in Ukraine. The mastermind behind the malware is not clear, but agencies point fingers towards Russia for this cyberattack. The reason for this is the tension across the Ukraine-Russia border these days.
According to New York Times, the code appear and deploy shortly after talks stalled among Russian diplomats, the U.S., and NATO. Further, Microsoft claims that the code looks similar to ransomware and designed to render targeted devices inoperable.
What is the Solution to Malware Detected on Ukraine Systems?

Source
Microsoft stated that all companies should investigate to know the origin of the malware. Also, every company should implement the defense through malware to protect data.
A Ukrainian security official told Reuters that the government believes the hackers are connected to Russia. They further stated that Russia’s intelligence services carried out the cyberattack on government websites in Ukraine. But, Moscow denied the involvement in cyberattacks against Ukraine.
How to Protect the System from Cyberattack?
According to Verizon’s 2019 Data Breach Report, about 28% of data breaches are connected to malware. It threatens every organization and is becoming more common every day. Countries and companies should both work hard to prevent their data from destructive malware.
Further, there is no solution to cyberattacks, but you can detect the malware and protect your system with smart moves. Here are some tips for you to save your computers or laptops from cyberattacks.
- Always choose a strong password for your private and confidential data files.
- Try to include at least eight characters with an uppercase letter, a lowercase letter, a number, and a symbol in the password.
- Enable multi-factor authentication on your system, such as a PIN or security questions in addition to a password.
- Do not save the password on your browser or your system. It is better to remember the password in mind.
Keep in mind that no software is completely safe against malware. But the software vendors regularly update their products to make them more defensive against viruses or cyberattacks. Install and update anti-virus software on your system to protect them from potentially destructive malware. Also, never share your password with anyone.
Conclusion
Malware infections can be devastating for organizations. By interrupting critical workflows and stealing or encrypting crucial data, it can cause serious financial and reputation damage. Protect yourself and your business from cyberattacks with effective cybersecurity. Also, perform regular backups to offline storage and keep changing your passwords to make sure your system is free from viruses.

by Anika D | Feb 4, 2022 | Industrial IoT, Information Technology
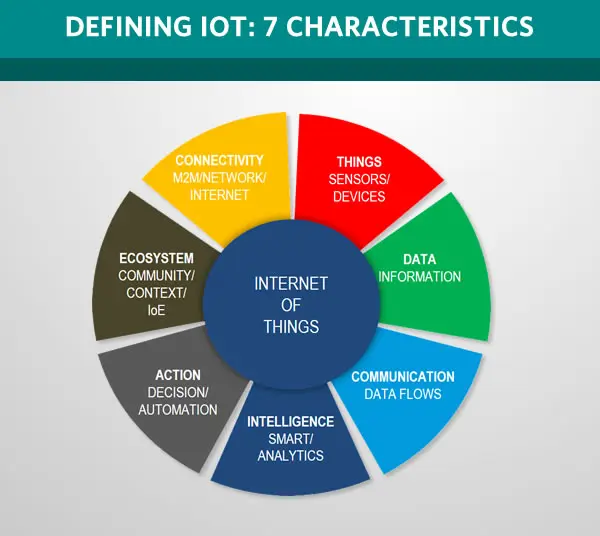
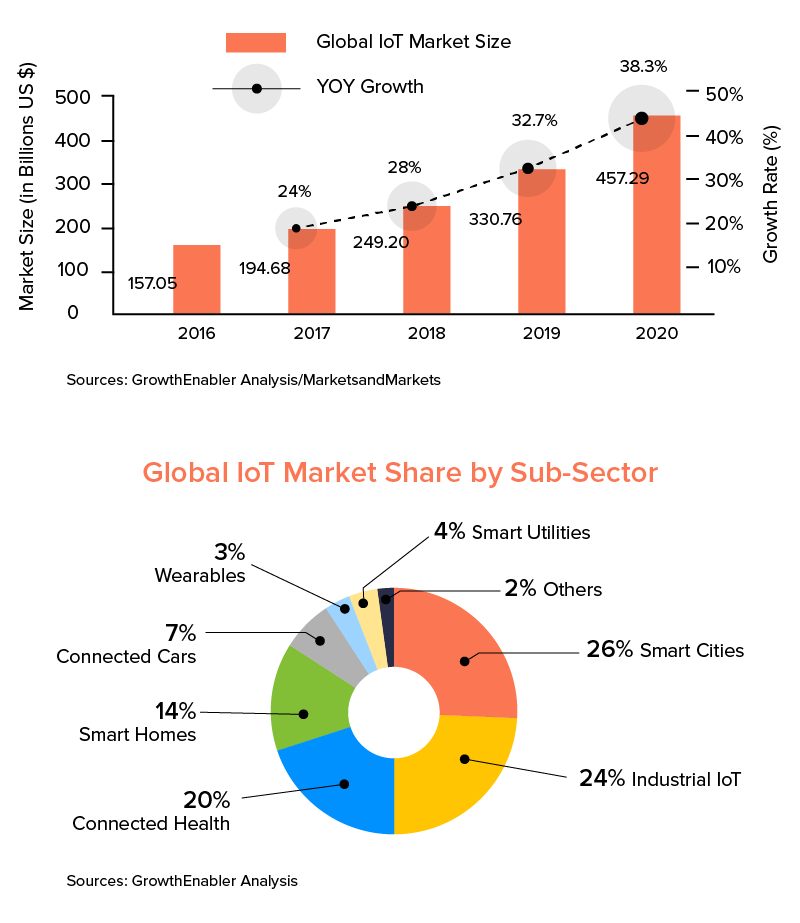
The internet of Things – IoT technology is around a billion devices connected to the internet which collect and share data. The rise in IoT witnessed a growth in the pandemic era as homes are new offices now. Up to 278 business executives plan to reduce their office space by 30% post-pandemic.
Such a change in work culture has made many tech tycoons introduce intelligent home features to reduce workload. Let’s check what the future holds for household chores in the arena of IoT.
Source
Smart Showers
Imagine a smart home alarm waking you up early because you’re on a hectic schedule today. The smart shower has already coordinated with data, and the water is heating at 105 degrees Fahrenheit. Everything is adjusted and customized according to your preferences.
Yes, it’s possible with IoT IoT technology and smart technology aiming to reduce household chores. Smart showers are powered by future-changing emerging technologies having sensors such as microchips, thermostats, voice control, and much more. It stores your weekly routine, collects new data, and works coordinates with the help of an app.
Home Cleaning and Laundry
The primary household chore is cleaning and laundry. IoT-driven applications like RFID technology will manage all your laundry. For example, there are smart laundry dispenser cabinets. It will collect clothes and wash them according to the amount of dirt.
Also, it will give alerts to residents about laundry schedules. In addition, they sort out the clothes and fold them after perfect washing and drying. The cleaning will become hassle-free with automated robots. It can map the house with tiny sensors and cameras. So daily it will be street cleaning like a punctual house help. They sense children on the floor, hindrances, and avoid stairs.
Kitchen Robots – IoT Technology
Doesn’t it feel like fantasy? But, it’s going to be true. The kitchen robots will use the latest sensors and cameras for cooking food. Moreover, the camera will use face recognition technology for sensing every family member.
Smart kitchen robots are versatile as various cuisines are stored in their memory. Further, robots connect with your smart home to work as a family member. They can store routine, behaviour, and data to give you a human-like cooking experience.
Shape-Shifting Furniture
Source
Reduce the tedious work of moving furniture as smart furniture is autonomous. Also, in the coming future, the Internet of Bodies will not look like computers but like usual elements of the home. To decrease your workload, tech capitalists are creating smart furniture.
They are app operated, can take their decisions, and are touch-controlled. Moreover, the furniture can turn the bed to an office chair, couch on just a command or judge the scenario. It will solve half of your work at home.
Bottom Line
By 2027, the IoT market will yield over $520 billion in market revenue, and the reasons are its immense benefits. Not only the household, but it’s taking over all the industries. It lets you focus on your primary goals to leave other tasks to intelligent gadgets. Another buzz is that it’s very energy-efficient and smart in all ways. So, look forward and stay updated with IoT technology to know what the future holds.
















