
by Anika D | Aug 16, 2022 | Industrial IoT, Information Technology
Before making the Internet of Things (IoT) strategy, you must know exactly what it is. The answer is pretty simple: IoT is the network of physically existing devices, objects, automobiles, etc. They consist of sensors and software chips that can collect or exchange data. In addition, IoT enables objects to control or sense the existing network’s infrastructure remotely. Here are some steps to jump-start the successful IoT journey:
Make a Business Case
Initially, decide the objectives and state the value proposition. Then, look into instances where you can create opportunities by connecting the objects. Also, determine how the machine data controlled by different sources can shrink operating charges, improve efficiency and make judgments for timely decisions.
Select the Right IoT Platform
Be careful about the risks of complexity that come with running multiple systems. Experts recommend a partnership with an IoT platform vendor that offers a unified framework for all IoT requirements. Many software vendors have invaded the market recently, showing IoT products. But few provide complete services and products.
Without a complete platform, you must depend on different partners for development. As a result, it will increase the complexity and system integration costs.
Build and Test
The IoT value chain is about integration, from edge devices to sensors, enterprise systems to gateways, and beyond. A major challenge to the promise of IoT applications is that a system must integrate all the IoT value chain components. But unlocking the potential of numerous intelligent things is difficult because of required communication standards.
Building IoT applications require a lot of time and resources. An IoT architecture with various APIs will simplify the interoperability task among heterogeneous objects.
Deploy – Internet of Things
The main asset of Internet of Things applications is sensor data. When the sensors generate a huge amount of data, inspecting and obtaining real-time insights is a major challenge. Therefore, prepare the business to control that magnitude, and data variety as the number of devices might scale.
From the functional point of view, complex algorithms need to transform the sheer data volume into business intelligence. It is important to have a powerful analytical tool to unlock the data value for business decisions.
Manage and Maintain
Managing remote assets is not so difficult when you ingrain big data, mobility, and cloud in your IoT architecture. Mobile applications complement IoT as you can control assets with a single move by receiving notifications and alerts in case of deviation in connected devices. For instance, a facilities manager for a mobile tower site may receive real-time information on the fuel status of the generator.
Similarly, a smartphone with in-built sensors acts as a connectivity hub with the ability to connect with the environment and paves the path for myriad applications. Clearly, IoT solutions are more valuable when mobile apps accompany them.
Final Thoughts
The future of the Internet of Things will be full of new inventions. According to experts, there will be around 20 to 30 billion devices connected to the internet by the end of 2022. This figure has kept on increasing in the last few years.
by Anika D | Aug 12, 2022 | Machine Learning
Machine Learning is all over the place; therefore, it is important to capture best practices and solutions to solve common ML problems. One of the simplest ways to catch these problems and provide answers is to design patterns.
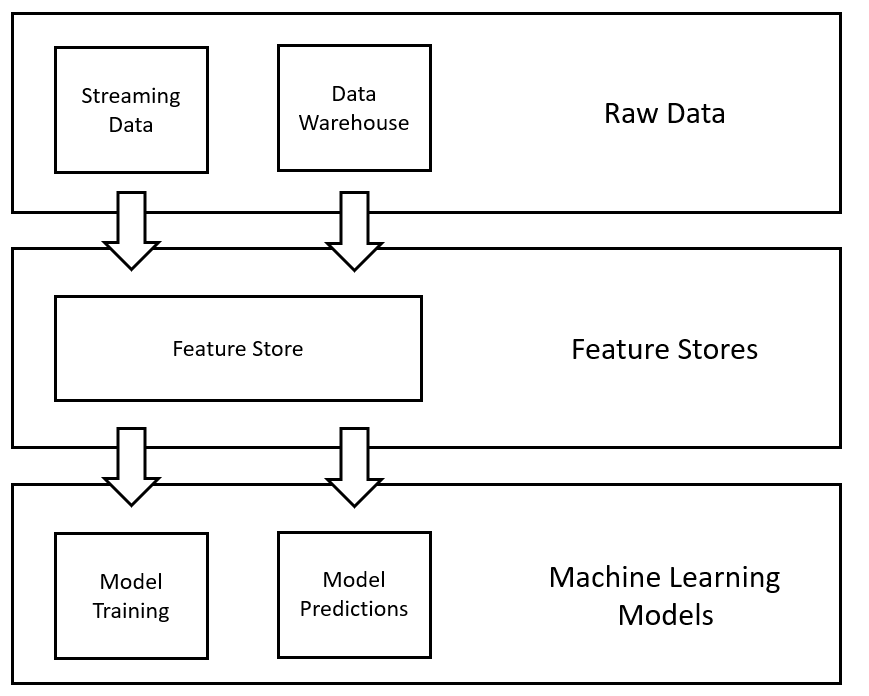
Source
“Design patterns” are the best practices used by programmers to solve common problems while designing a system or an application. Below are a few design patterns that you must try:
Problem Representation Design Pattern: Rebalancing
The common scenario in classification problems like Fraud Detection, Spam Detection, or Anomaly Detection is Imbalanced datasets. But typical Machine Learning models for such classification work by assuming that all the classes are balanced and result in poor predictive performance. Some of the common strategies to handle imbalanced datasets are as follows:
- Choose Right Performance Metric: AUC or F1 scores are efficient for performance evaluation as the goal is to maximize precision and recall.
- Sampling Methods: Resampling is widely adopted to balance the dataset classes’ samples.
- Weighted Classes: It involves penalized learning algorithms to increase the misclassification cost in the minority class.
Reproducibility Design Pattern: Transform
The idea of this reproducibility design pattern is to separate input from features. You have to extra features from raw input to train a model. But in most ML problems, you can not use input directly as feature. Instead, you must apply various transformations like scaling, standardization, encoding, and others to reproduce them at the prediction time. So, it is vital to separate the inputs from the features, encapsulate the preprocessing steps, and include them into the model to ensure reproducibility.
Model Training Design Pattern: Checkpoints
The major attributes of a scalable system are resilience and fault tolerance. The snapshot of the model’s internal state is the checkpoint. So, you can resume training from this state to another later. However, during the activity, power outages, task preemptions, OS faults, and other unforeseen errors can happen, resulting in time and resource loss.
Reproducibility Design Pattern: Workflow Pipeline
The goal of the design pattern is to isolate and containerize the individual steps of a machine learning workflow into an organized workflow. It ensures scalability and maintainability. Generally, the machine learning development workflow is generally monolithic, containing a series of tasks from data collection to model training and evaluation. But the machine learning tasks are iterative.
Tracking the small changes in the workflow during the development process becomes complicated as the process iterates many times. It introduces the concept of MLOps, similar to DevOps concepts like continuous integration and continuous delivery. The key difference between MLOps and DevOps is that it is not only the code. It is also the data that must be continuously tested and validated in MLOps.
Responsible AI Design Pattern: Explainable Predictions
Generally, machine learning models are black boxes. But it is important to clearly understand the model behavior to diagnose the errors and identify potential biases. The major factor in Responsible Artificial Intelligence is introducing explainability in machine learning. Hence, the key idea is to interpret the machine learning models to understand why and how the model made the predictions in a certain way.
Final Words
You can implement the above-mentioned techniques in most machine learning practices, but defining design patterns helps to create general reusable solutions for common problems. In addition, they help to communicate with engineers and solve problems by providing off-the-shelf solutions.

by Anika D | Aug 9, 2022 | Emerging Technology
The 5G network helps to collect a significant amount of on-road vehicle data. This information can serve various purposes, such as carrying out road maintenance, providing road weather services, and controlling self-driving cars. So, the ultimate goal is to reduce the number of road accidents.
VTT’s two-year 5G-Safe project explored various possibilities of improving road safety with 5G. Using a fast 5G network, you can collect many sensors, video and radar data. Then, you can transmit information automatically in real-time without the driver’s help. Furthermore, when processing this data via intelligent systems, you can send warnings to road users, maintenance, and third parties.
Please Slow Down near Icy Corner
One of the key applications for vehicle data collection is local road weather services. In the future, you can send real-time weather information or warnings to drivers’ satellite navigation devices. So, drivers can use this information to follow a different route while driving. In the final pilot, the 5G-Safe project showed safety and weather-related services delivered to vehicles via the 5G test network. These services included traffic safety alerts, road weather forecasts, and weather alerts.
You can transmit some automated weather warnings via the current 4G networks. However, sending real-time video footage between vehicles needs considerably more network capacity and low latency. The 5G network can support both.
Crowdsourcing Information for Road Maintenance
Source
5G emerging technology opens up new possibilities from the road maintenance perspective. This technology provides an efficient way to collect information on the road’s condition. The 5G-Safe project illustrated the usage of data to alert road maintenance providers about the range of issues that requires attention. For instance, snowy traffic signs, snow build-up on the roads, or potholes.
It is a great improvement on the current approach, where road maintenance contractors are responsible for information collection. If you can crowdsource monitoring to all road users, road maintenance contractors can work more efficiently and cut their costs. In addition, with comprehensive and reliable data, road contractors can prioritize urgent jobs.
Self-Driving Vehicles Expand their Territory
Source
Though 5G technology helps human drivers, its impact on self-driving cars can be more revolutionary. You can use real-time data to better control self-driving cars and change their behavior as per observations. VTT’s 5-G safe self-driving car Martti has already tried these possibilities.
In the final pilot, Martti drove in automated mode on the test track utilizing its warnings and sensors. MEC service gave warnings to Martti by detecting obstacles on the road in real-time. In addition, Martti received alerts of slippery roads from the weather service. Based on these warnings, the robot car could plan its route to avoid dangerous stretches.
Precise information is important in challenging conditions and expands the potential uses of self-driving cars. Currently, people use self-driving cars mostly in areas with non-problematic weather conditions. Controlling self-driving cars in the Nordic climate needs accurate real-time data. The 5G technology allows it to collect data from areas beyond the cars’ sensors.
Final Words
There is a huge interest in global services and solutions that improve road safety. So, many companies are currently planning further development of road safety solutions using 5G technology.

by Anika D | Aug 5, 2022 | Cybersecurity, Emerging Technology, Information Technology
Emails are part of every business in today’s world, but it is also one of the biggest security risks. BEC (Business Email Compromise) is rising every year. In addition, it is becoming common for criminals to use different phishing and spoofing attacks to probe organizations. In recent years, Ransomware has been growing rapidly and poses a greater risk to companies. What you don’t know is that email is a common entry place for Ransomware.
Source
But no need to worry about this. There are some countermeasures to this issue. These email security practices can go a long way for organizations from several threats. Here are some best practices to avoid Business Email Compromise:
Use Strong Passwords
It would be best to use strong passwords that meet the following criteria:
- It must complete a minimum length requirement.
- It must contain letters and numbers.
- It must contain both lowercase and uppercase letters.
- It may not have full name data.
- It should not be a commonly guessed password like 123456 or abcdef.
Use 2FA (Two-Factor Authentication)
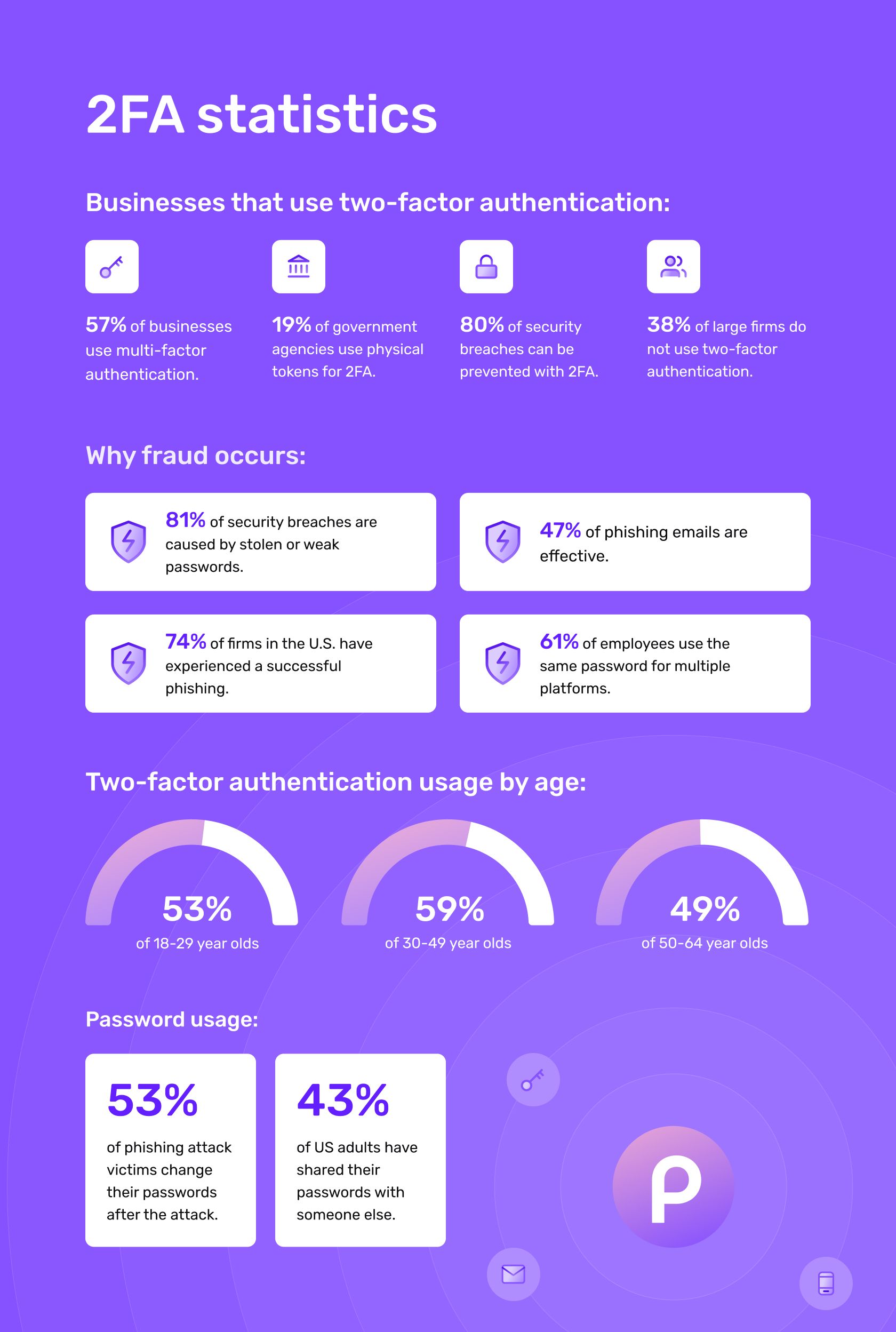
Source
Many people think that only professionals can do 2FA, but it is not a difficult task. It is more like adding another shield to the account. Thankfully, almost every platform offers 2FA, but you can use another email provider if your system doesn’t support it. Also, if a hacker guesses your password, 2FA will stop them from entering before they get a sneak peek of your emails. Usually, two-factor authentication codes are sent to you by email, SMS, voice calls, or OTPs.
Be Careful of Suspicious Attachments
Nowadays, file sharing in the workplace mostly happens via collaboration tools like OneDrive, Dropbox, or Sharepoint. Therefore you should treat every file attachment in the mail suspiciously, even if it is from your colleague. Be more careful about the attached file with unfamiliar extensions or one that commonly delivers malware payloads (.zip, .exe, .scr, etc.).
Never Access Your Emails from Public Wi-Fi
If you take the office devices home or open your work emails from personal devices, do not access emails on public Wi-Fi. It is because cybercriminals can easily discover data passing through publicly accessible Wi-Fi. So, your sensitive data and login credentials both are at risk. Accessing emails is best when you are confident about network security. Opt for a safer option using mobile data or internet dongles outside the office.
Change Password Regularly
Many people keep passwords for years. But it is one of the biggest cybersecurity mistakes. The simplest yet most effective email security practice is regularly changing passwords. You must ensure the following things:
- Have a new email password after every 2 to 4 months.
- Use devices or do it yourself instead of leaving it to other people to update credentials.
- Do not add one of two characters to the current password when creating a new one. Change the entire password.
- Do not use passwords that you already used in the past.
Wrapping Up
BEC is a criminal phenomenon that has potentially severe consequences. BEC criminals usually live outside the country, so it is difficult for law enforcement to prosecute them. Therefore, prevention and detection are crucial. So, all companies should educate their employees and create an environment encouraging compliance.

by Anika D | Aug 2, 2022 | Artificial Intelligence, Information Technology
Have you noticed that your various accounts require multiple identity verification methods when you log in these days? You can no longer access your email, accounting system, or cloud applications by only entering your username and password. Instead, you need to enter a short code you receive on your phone or via email. Sometimes, you can also get verification calls using biometric data or a smart card.
Do you know what this is? It is multi-factor authentication (MFA). It consists of three things that you combine for identity verification. You can summarize MFA as “something you are, something you have, and something you know.” For instance, a combination of tokens, a username, password, or biometrics.
Source
Setting multiple verification methods may seem like a hassle, but it makes your accounts secure. Below are some reasons to enable MFA:
Secure Incase Passwords Get Stolen
These days password theft is evolving. Cybercriminals’ main methods to steal passwords are keylogging, phishing, and pharming. Keylogging involves secretly recording keys that strike on a keyboard. Phishing consists of fraudulent calls, emails, or SMS that ask for your sensitive information. Pharming includes installing malicious code on the device that redirects users to fraudulent sites.
Any individual or enterprise can easily become a victim of these attacks. But MFA ensures that your identity and accounts remain secure even if your password gets leaked.
MFA Adapts with Change in the Workplace
These days employees work outside the companies. So, with change in the workplace, you need more advanced MFA solutions that manage complex access requests. MFA offers multiple protection layers and evaluates potential risks while looking at the user’s location and device.
For instance, if you log in from your office, you will not get a prompt message for additional security factors. But if you log in from a café using your mobile, you will receive an SMS for verification of another factor.
Reduce the Usage of Unmanaged Devices
These days companies have embraced the remote working concept. So, employees often use personal devices or less secure internet connections. A hacker can easily install password-stealing malware on the device due to a compromised router. When you use MFA, you don’t have to worry about the security of unmanaged devices.
Improve Employee Productivity and Flexibility
Remembering so many passwords can be a huge burden. Therefore, many people use simple code, but that is easy to crack. To avoid this, many companies enforce password policies encouraging employees to set stronger passwords and update them regularly. But a new issue of forgetting the password arises with it.
Forgetting the password means password resetting, and it costs more time. In such cases, MFA allows you to sign in via a single-use code generated by an app or a fingerprint scan.
Stay Compliant
If your company deals with personally identifiable information or finances, state or federal laws may need an MFA security. MFA ensures access to protected health information by only authorized users. So, it allows your firm to remain compliant with HIPAA (the Health Insurance Portability and Accountability Act).
To Sum Up
Multi-Factor Authentication methods are quite inexpensive and easy to deploy. In addition, they provide a simple, effective solution to users and a wider business network. So, ask yourself why you haven’t already adopted this cybersecurity plan and go for it as soon as possible.










