
by Anika D | Jan 26, 2022 | Cybersecurity, Emerging Technology, General, Industrial IoT, System Engineering
Software development is one of the highly paid career fields. The average salary of a software engineer is higher than the income of people for many other industries. So, the more experience a software engineer has, the higher their salary will be. But all software development careers are not the same.
There are several fields within software development with their own set of rules. The income range of software engineers varies across different domains. In addition, location also matters. For instance, software engineers in SanFrancisco, New York, or Seattle often earn more than people working in other areas of the United States.
The following are some most profitable software engineering roles:
Cybersecurity Engineers
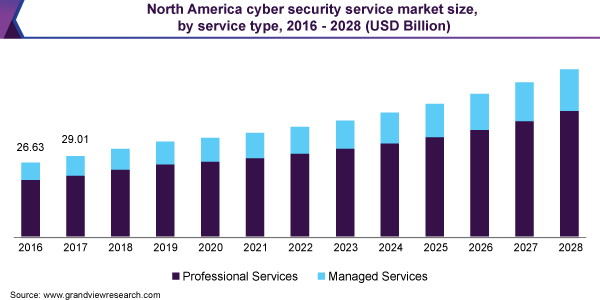
Source
With the increase in digitalization, cybersecurity is becoming a highly-valued function. It is in demand by various tech companies and several other industries like financial services, banking, healthcare, etc. They prefer it to avoid different security threats. Because of their high demand, their average salary is also high.
Video Game Development
Many professionals are working in the high-paying video game development field. Usually, game developers manage the process of developing a custom video game. You will typically plan gaming concepts, generate storylines, and create custom visual graphics when you work in this field. Simultaneously, you will write a functional game code that involves coding the base engine.
If you want to opt for a career path, you need great critical thinking, storytelling, and time management skills. Simultaneously, you will need expertise in programming and multimedia development. Indeed, a video game development career is a high-paying opportunity.
Cloud Development
Cloud development is a new field of software engineering, but it is rapidly growing with many job opportunities. This is essentially involves designing, planning, and implementing the structural architecture with cloud delivery models.
If you want to follow career paths in cloud development, it is essential to be proficient in network management, database maintenance, and coding. Pursuing job opportunities in cloud development, you can get jobs with high-paying salaries.
No-Code or Low-Code Developer
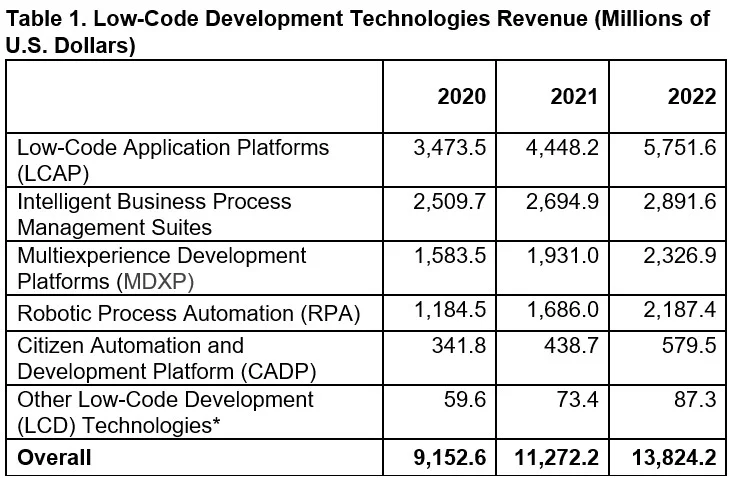
Source
The no-code and low-code development tools opened up various opportunities for companies to quickly create software without hiring developers. These tools enable you to create a web or mobile app in hours rather than weeks. Therefore, more companies are embracing low-code or no-code apps.
No-code jobs are good career fields to start. You will find a variety of pay scales and required skills, yet your coding background undoubtedly proved to be an asset.
Database Administrator
Database administrators handle provisioning, scaling, security, and optimization of data storage systems. You do not need any knowledge about security best practices, SQL and NoSQL databases, and basic scripting skills. So, you will also worry about minute optimization issues like fixing caches and indexes.
If you are a beginner in software development, begin learning about databases. You will have to know about appropriate database applications and how to optimize them at scale. This profile is in high demand because of good salary packages.
Final Thoughts
Software engineering is a great field, but it is not suitable for everyone. However, even if you don’t work for it, the skills won’t get wasted. Instead, you can look for one of the career paths mentioned above and earn more.

by Anika D | Jan 24, 2022 | Business, Cybersecurity
Cyber security strategy is a noteworthy action plan for the organization to secure its assets in the coming years. However, with the emerging technology, cyber threats also change unpredictably. So, you definitely have to upgrade your strategy. It is purely guesswork about what you need to do.
The deliberate result of developing and executing a cybersecurity plan is that the assets are secure. Generally, it involves switching from a reactive to a proactive cyber security approach. There you focus on preventing the cyber threats rather than reacting against them. As a result, you will secure your organization network.
Source
Your organization can maintain its reputation and reduce threats to its employees by preventing trivial incidents from becoming crucial. However, creating cyber security for the business takes time and effort. But it also means distinguishing between beating your competitors and moving out of business in the future. Below are some basic steps to develop your cyber security strategy:
Step 1: Create an Effective Security Structure
-
Determine What you Want to Protect
Understand the assets that your company needs to protect. Although you cannot shield everything fully, focus on what you definitely have to save first and what can happen in the absence of security. Review all business processes and understand how to generate revenue by the company and what systems can disrupt by being unavailable. Also, identify the critical data and IT assets like devices, applications, users, and servers for your business.
-
Determine What you Need to Protect Legally
While security and compliance are not the same, most organizations depend on the CISO for maintaining security compliance frameworks. Non-compliance is expensive and threatening for your business. Ensure that you design the cyber security plan with compliance frameworks and plan legal requirements.
-
Understand the Company’s Risk Appetite
Before creating a cyber security strategy, understand your organization’s risk assessments. Also, learn the amount of risk your organization can accept while pursuing strategic objectives. Risk appetites depend on the industry, the company’s financial strength, goals, and many more.
The cyber security plan for a startup won’t work for an established corporation. By learning the company’s risk appetite, ensure that you are not under-or-over protecting the business.
Step 2: Understand the Threat Landscape

Source
After learning what you have to protect, analyze and understand the threat landscape. Initially, understand the company’s environment for its operations. Know your potential customers, product or service you sell, disrupting the business benefits, etc. The questions help you learn about the general environment.
Also, learn about your competitors, threats they face, a security breach in the past, etc. The threats faced by competitors may also affect your business. Finally, learn about the type of threats you need to protect your business from and potential attackers. You can be well-prepared in defending the business by learning the answers to these questions.
Step 3: Create a Strategic Cyber Security Plan
-
Pick a Framework, Identify Current State of the Security Environment, and Build a Timeline
Source
Select a framework such as ISO, CIS Controls, and NIST to build a cyber security plan. It is essential to pick a framework to track progress effectively while prioritizing the critical steps. For example, the CIS Controls gives you a set of prioritized actions to save your organization and take these actions. In addition, it enables you to track progress to know what you have to do.
Once you know what you need to protect from the risk management point of view, evaluate current security measure effectiveness. Decide on a timeline, depending on the current security state. Things will change with time, needing occasional changes in the timeline. However, it is necessary to set a target timeline to get to your organization’s best risk level.
-
Evaluate Company’s Security Maturity Level
Evaluate the organization’s security maturity level using either outside consultants or in-house staff. Security maturity means a company’s adherence to security best processes and practices; measuring it allows you to identify areas for improvement.
Whether hiring a consultant or analyzing yourself, ensure that the process is repeatable. In this way, when you determine the security maturity in the coming years, you will have a benchmark for results comparison.
-
Evaluate the Technology Stack
Look at your current technology and identify tools you don’t use to their full benefit. Underutilized tools cost you time, money, and increase the attack surface. Then, find out the proper solutions to fulfil their original purposes. In addition, you can use the Cyber Defense Matrix to find security gaps. The Cyber Defense Matrix helps you understand what you need and which products solve your problems.
-
Identify Quick Wins and Foundational
While creating a cyber security strategy, identify the quick wins, foundational and high-risk items you must address initially. Then, identify future steps of the plan and prioritize actions. Quick wins are easy to fix things. Therefore, ensure that you have both quick wins and foundational tasks in the beginning.
Step 4: Evaluate Organization’s Ability to Execute a Cyber Security Plan
Finally, assess if your organization can get the necessary work done for security. Observe your current security and IT teams to understand their bandwidth and skill sets. If you don’t have the required resources, outsource some security work or augment your team members to execute the cyber security plan.
During this step, think about the future of your IT team or the business. Then, see if your IT team can handle any company-wide large-scale projects in the future.
Final Thoughts
The cybersecurity strategy development and implementation is an ongoing process and will face many challenges. Critically, it is important to monitor and reassess the organization’s cybersecurity maturity to measure the progress toward your objectives. The earlier you identify the falling area, the sooner you can report it to catch up.
Measuring progress includes tests and exercises, internal and external audits that simulate future events under various circumstances. Finally, rethink your cybersecurity strategy if a new threat arises. Agility in cyber security is very important. Don’t hesitate to update your plan with changes in security technologies and cyber threats. Or upgrade if your organization acquires new assets that require safeguarding.

by Anika D | Jan 17, 2022 | Business, Cybersecurity, General, Information Technology
The legal industry has transformed significantly over the years and will remain growing at a significant pace. As a result, various law firms worldwide are increasing their annual investments in voice technology. Voice technology gives a new face to the legal industry by providing several opportunities for market expansion, client experiences, or remote working. In addition, legal firms emphasize using voice technology to improve security, data storage, and other factors.
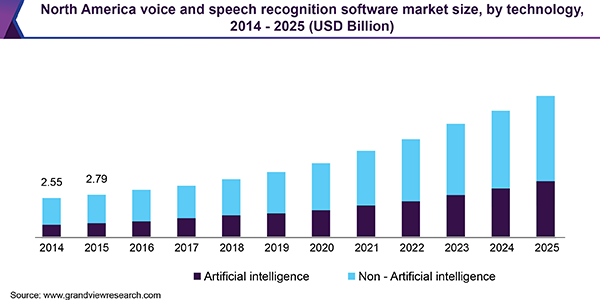
Source
Why Depend on Voice Technology?
Voice recognition helps to improve the productivity of corporate legal departments and law firms by supporting the tasks listed below:
- Reduce dependency on support staff
- Minimize document turnaround and streamline documentation efforts
- Dedicate extra time to understand the demands and problems of clients
- Lower transcription expenditure
- Focus on a business that can cross a lawyer’s desk.
You can easily achieve these tasks without changing existing information systems or processes. Voice recognition technology holds language modeling to determine and differentiate within millions of human expressions that produce a language. It uses statistical models for analyzing and interpreting incoming streams of utterances.
The latest advances in voice recognition significantly improve detection accuracy, performance, and usage ease. For example, Google’s Cloud Speech-to-Text can detect 120 languages and has attained 95 percent accuracy in the English language. These types of accomplishments are creating amazing discoveries in the legal domain.
Voice Technology Empowers the Legal Work
Each legal professional uses voice technology for several purposes, depending on their responsibilities and roles, workflow adjustments, and other needs. The primary beneficiaries of voice recognition in the legal industry are:
- Judges
- Attorneys or Lawyers
- Support Staff or Assistants
- Court Reporters
- Partners and Associates
- Law Students
- Transcriptionists
- Paralegals
- Legal Researchers
Voice technology in the legal domain includes the following applications:
-
Documents creation and management
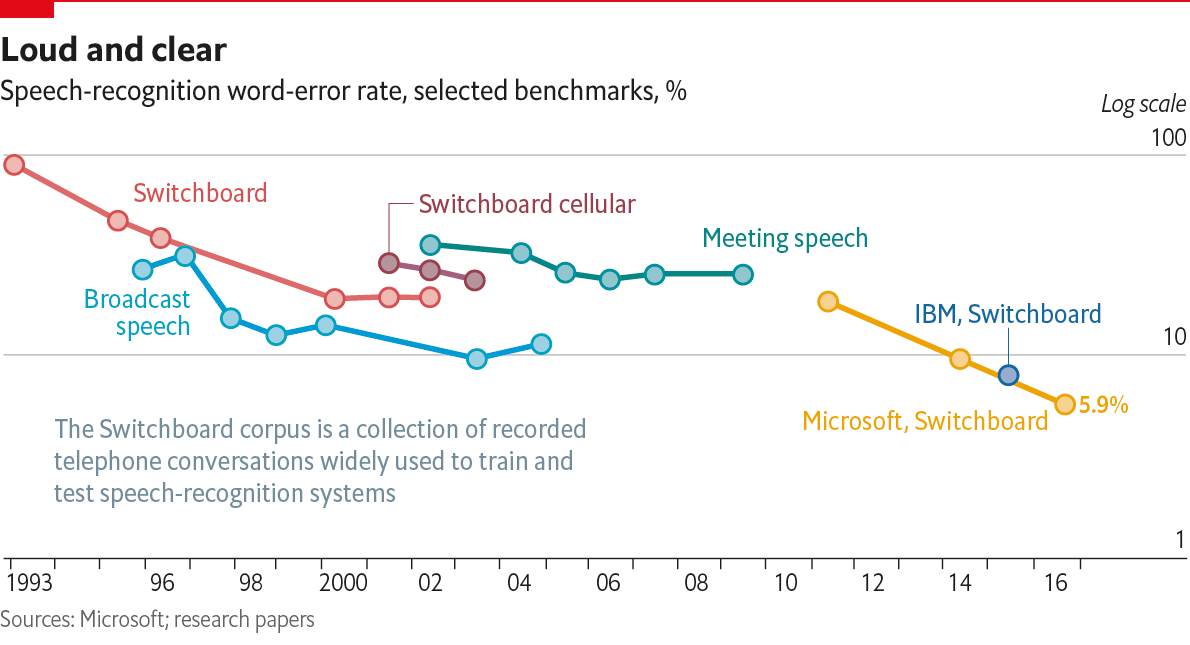
Source
Law firms depend on paralegals, legal secretaries, or external transcriptionists to decipher the documents like legal briefs, client memos, contracts, and deposition summaries. It will hike the administrative charges of the law firms and extend the dictate – transcribe – review – edit cycle causing customer dissatisfaction.
A lawyer can dictate the document to their system instead of manually typing it using voice recognition software. This software transcribes the dictation automatically that you can review later to check accuracy.
-
Contract Review Automation
In most law firms, manual contract reviews consume considerable time and resources. AI-enabled word analytics offers the ability to analyze and review documents automatically with human-like knowledge. Application of Natural Language Processing (NLP) and data capture techniques allow us to identify facts, key sections, entities, or clauses from contracts and business documents. It also enables us to determine if the agreements meet the set criteria.
-
Audio and Text Summarization
A lawyer cannot replace voice recognition software’s impressive and fast processing power while surfing through large data. The voice recognition and analytics tool uses machine learning models to deliver precise summaries of lengthy documents. As a result, it can be useful for incorporating large information into a short report in legal work.
Bottom Line
Voice recognition APIs enable companies to look at call data surfacing details that empower legal professionals to care for their clients. Instead of randomly reviewing the small number of calls, lawyers use voice recognition softwares for proactive intervention.

by Anika D | Apr 9, 2021 | Cybersecurity, Industrial IoT
Unauthorized attempt which could expose your personal data defines cyber-attack. It could include installing spyware or phone tapping without your permission. With the increase in cyber-crimes, we witnessed some major cyber-attacks in 2020.
Common Cyber Attacks In 2020
SolarWinds
SolarWinds was one of the most talked cyber-attack. Eminent companies like Microsoft etc. were also affected by it. The server that gives access to updates of SolarWinds was compromised and thus attacked. This code allowed information modification.
Twitter
Apart from this Twitter was also in the news lately. It was observed that fraudulent information regarding bitcoin was posted. The user apparently asked the twitter account holders for Bitcoin and through this received more than $100,000. Bill Gates, Elon Musk, Kanye West etc. were some of the famous personalities that were targeted.
Marriott
You think your data is safe with hotels? Well data of almost 5.2 million guests of Marriott were accessed. Marriott is one of the most eminent hotels throughout the world. The information included the name, birth date, phone number, address etc.
Zoom
Zoom was another such application that was attacked by hackers. Government also released the statement that zoom was not safe to use. Also, zoom codes were not so hard to crack so anyone could join in the meeting and get access to all the confidential data of the company. However, zoom has now hired an intelligence firm to look over the safety.
Greek Banking System
All of us have heard about the Greek Banking System. A Greek travel site was hacked due to which a lot of debit and credit cards were cancelled by the 4 main banks of Greece due to security protocols. A few customers were also charged with undesirable transactions. This website was a travel website and was used to book tickets etc.
MGM
MGM was another travel related incident that was exposed to cyber-crime. Personal data of around 10.6 million guests was at risk. MGM resort is a global entertainment company accompanied by resorts and casinos. Information of Famous personalities like Justin Bieber, Jeff Bezos was also at risk.
Finastra, was also attacked by a ransomware in which it was temporarily disconnected and thus affected servers from the internet. Though there is no evidence that the data of the employees were exfiltrated it did disrupt the operations.
Let’s Take a Look At The Statistics
Today, cybercrime has affected more than 50% of businesses. Human errors are responsible for 95% of it. It is a shame but only 5% of company’s folders are the ones which are properly protected. There were 11,762 cases Between January 1, 2005, and May 31, 2020
It is seen that in the first half of 2019, attacks on IoT devices have tripled. A whopping amount of $3.92 million has cost enterprises due to data breaches. Due to COVID, cybercrime has increased up to 600%.
To conclude we can say that cyber-crime is a punishable offence. There are several laws against it. By being a little more attentive we can help in stopping the spread of cyber-crime. Cyber-crime violates basic human laws too. It is time, let us take a stand against it.

by Anika D | Feb 24, 2021 | Cybersecurity, Data Science
While many sectors including manufacturing are using AI and modern technologies, many healthcare facilities are still unsure. Mostly because the large data collection makes them easy targets and the past records.
For instance, February of 2020 alone marked 39 data breach cases in healthcare. More than 1531,855 records got exposed.

Source
So the government has strict codes for the healthcare sector. They have to follow it to avoid legal conflicts and ensure users’ security.
Here’s a little detail about the risk this sector faces and the tricks it’s following to prevent the breaches.
Risks
There are multiple risk possibilities in using high-end and automated technologies including cloud storage in healthcare. The most common of them is the data breach risks.
Since the system connects with the internet and uses it to store, manage and access the data, it’s vulnerable to cybercrimes. If anyone gets access to the data, they will have access to every confidential detail of the patients. It can also compromise data about the finances of the firm.
Another risk in this sector is an indirect or direct release of details. While it’s a rare scenario. There are cases where a private organization sold/released their user data.
Cracking Data Privacy Code
The data privacy code states that any personal data that a person including a staff member shares with healthcare is confidential. The healthcare center and anyone connected with it has to ensure its safety.
The following are some tricks and measures that the healthcare sector is currently using for this part.
Secure Access
Every system connected with healthcare needs a proper credential to access the information. Some facilities also use dual check and timed login features for this part. The online database also used firewalls and sometimes data science firms to detect system anomalies.
Encryption
Converting the data into a different form is common for most websites. The healthcare facilities assign a cipher key to every entry and save it as a hex code. This way, even if someone gets the hacks, all they see will be codes. The cipher key further ensures that the methods like brute force or guessing don’t work.
Sophisticated Security Checks
Even with precautions, there are always possibilities of hacks and patches. So, healthcare facilities often interact with data science and automation firms to introduce analytical applications in their system. These systems help use the network data and past data to predict unwanted activities on it. The data is helpful in finding system weaknesses and fixing them.
Controlled Third-Party Access
The healthcare centers get regular visits from a number of people, including general visitors, patients, maintenance workers, and vendors. Many like the maintenance worker may even need to use a computer at the center. So, it’s a common policy to lock the patient information.
Proper Disposal of Devices
The IOT based medical devices store data about their users and sometimes the staff member associated with them. Throwing it without wiping is a big risk, even if it’s broken or non-functional. Mostly, the healthcare centers have specified disposal for them. They are locked out of reach and then destroyed or wiped to extend that no one can recover data from them.
System Misuse
One of the most common causes of data breaches in Healthcare is system misuse. 71.7% times it’s the LAN accessed system that causes the data breach. Training staff members and restricting the use of any external storage device is one way to prevent this issue. Restricting non-trusty websites and monitoring systems is also effective.

Source
Final Words
Data privacy code is essential to ensure that everyone associated with the healthcare sector gets security. The hospitals are taking strict measures to ensure their compliance with these codes. This combined with other technologies like 5G is sure to revolutionize the industry.

by Linda Rawson | Feb 5, 2021 | Cybersecurity, Information Technology
A cyber-resilient mindset is different from a cybersecurity mindset, although they are complimentary. Cybersecurity has often been an afterthought in System Engineering. It always surprises me to read through diagrams or models and discover not one mention of cybersecurity. Criminals will exploit humans and systems to bring the system to its knees and cause massive revenue loss.
Security in System Engineering has a lot to do with WHO is involved more than vulnerabilities. The most important thing for System Engineering security is in changing the culture to embrace security. No exceptions. Security must be built into the project at the beginning.
Implementing a DevSecOps approach ensures that security, development, and IT Ops teams work toward a joint security goal. ~ Linda Rawson
The People are Not the Process.
DevSecOps is agile in nature, and the people are still involved but not in the same capacity as they were in the Waterfall model. In DevSecOps, the people are not the process: The pipeline, the set of phases and tools that the code follows to reach deployment, defines the process.
The phases include Build, Test, and Deployment and prefer automation over manual methods. Build automation consists of the tools needed to grab the code and compile it. Test executes the automated test cases, while deployment drops the build into its destination. It means using static analysis tools that check the portions of code that have been changed versus scanning the entire code base.
The People Monitor the Process and Respond to Process Failures
Training hardware and software developers regularly on new cyber-attack techniques and exploitation vectors is essential to application solution security. Security and quality assurance policies need to be promulgated among the team to make development standards unambiguous and clear for everyone. Defensive Coding Practices result in more complicated code but writing code while thinking how an attacker might think, reduces vulnerabilities, and therefore reduces risk.
All Levels of Management Must Be Involved
Individuals from government stakeholders, operations, security, and development teams must be encouraged to have a cyber-resilient mindset. If you are proactive and think like a cyber attacker, you would do things differently instead of explaining why an attack occurred. In the case of an extensive enterprise system, why bank accounts were drained, or an airplane hit the ground.
Adopting Cybersecurity Practices
Adopting cybersecurity practices such as continuous integration, continuous delivery, and constant distribution has dramatically accelerated the speed at which organizations release and update applications. Security is no longer something that can be bolted on at the end of the development cycle but must be started by a proactive organization.
This blog was written by Linda Rawson, of DynaGrace Enterprises (dynagrace.com). For further information, please connect with Linda on LinkedIn, or contact her at (800) 676-0058 ext 101.
#systemengineering #cybersecurity #cybersecurityawareness #DevSecOps #infosec #security #mindset















