
by Anika D | Jan 26, 2022 | Cybersecurity, Emerging Technology, General, Industrial IoT, System Engineering
Software development is one of the highly paid career fields. The average salary of a software engineer is higher than the income of people for many other industries. So, the more experience a software engineer has, the higher their salary will be. But all software development careers are not the same.
There are several fields within software development with their own set of rules. The income range of software engineers varies across different domains. In addition, location also matters. For instance, software engineers in SanFrancisco, New York, or Seattle often earn more than people working in other areas of the United States.
The following are some most profitable software engineering roles:
Cybersecurity Engineers
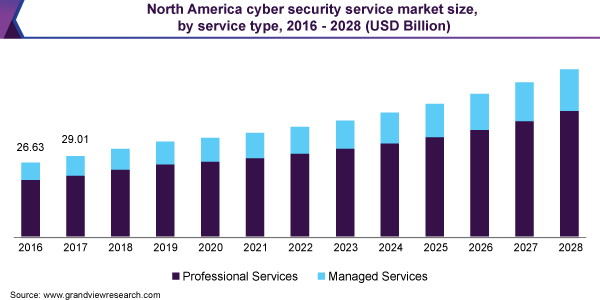
Source
With the increase in digitalization, cybersecurity is becoming a highly-valued function. It is in demand by various tech companies and several other industries like financial services, banking, healthcare, etc. They prefer it to avoid different security threats. Because of their high demand, their average salary is also high.
Video Game Development
Many professionals are working in the high-paying video game development field. Usually, game developers manage the process of developing a custom video game. You will typically plan gaming concepts, generate storylines, and create custom visual graphics when you work in this field. Simultaneously, you will write a functional game code that involves coding the base engine.
If you want to opt for a career path, you need great critical thinking, storytelling, and time management skills. Simultaneously, you will need expertise in programming and multimedia development. Indeed, a video game development career is a high-paying opportunity.
Cloud Development
Cloud development is a new field of software engineering, but it is rapidly growing with many job opportunities. This is essentially involves designing, planning, and implementing the structural architecture with cloud delivery models.
If you want to follow career paths in cloud development, it is essential to be proficient in network management, database maintenance, and coding. Pursuing job opportunities in cloud development, you can get jobs with high-paying salaries.
No-Code or Low-Code Developer
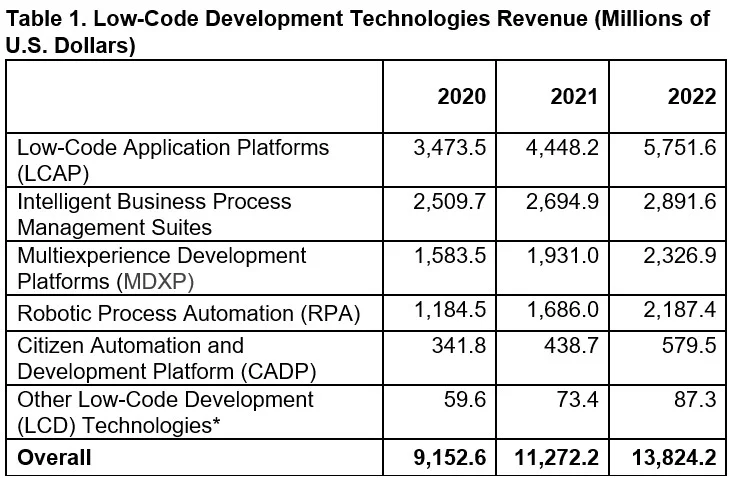
Source
The no-code and low-code development tools opened up various opportunities for companies to quickly create software without hiring developers. These tools enable you to create a web or mobile app in hours rather than weeks. Therefore, more companies are embracing low-code or no-code apps.
No-code jobs are good career fields to start. You will find a variety of pay scales and required skills, yet your coding background undoubtedly proved to be an asset.
Database Administrator
Database administrators handle provisioning, scaling, security, and optimization of data storage systems. You do not need any knowledge about security best practices, SQL and NoSQL databases, and basic scripting skills. So, you will also worry about minute optimization issues like fixing caches and indexes.
If you are a beginner in software development, begin learning about databases. You will have to know about appropriate database applications and how to optimize them at scale. This profile is in high demand because of good salary packages.
Final Thoughts
Software engineering is a great field, but it is not suitable for everyone. However, even if you don’t work for it, the skills won’t get wasted. Instead, you can look for one of the career paths mentioned above and earn more.

by Anika D | Jan 24, 2022 | Business, Cybersecurity
Cyber security strategy is a noteworthy action plan for the organization to secure its assets in the coming years. However, with the emerging technology, cyber threats also change unpredictably. So, you definitely have to upgrade your strategy. It is purely guesswork about what you need to do.
The deliberate result of developing and executing a cybersecurity plan is that the assets are secure. Generally, it involves switching from a reactive to a proactive cyber security approach. There you focus on preventing the cyber threats rather than reacting against them. As a result, you will secure your organization network.
Source
Your organization can maintain its reputation and reduce threats to its employees by preventing trivial incidents from becoming crucial. However, creating cyber security for the business takes time and effort. But it also means distinguishing between beating your competitors and moving out of business in the future. Below are some basic steps to develop your cyber security strategy:
Step 1: Create an Effective Security Structure
-
Determine What you Want to Protect
Understand the assets that your company needs to protect. Although you cannot shield everything fully, focus on what you definitely have to save first and what can happen in the absence of security. Review all business processes and understand how to generate revenue by the company and what systems can disrupt by being unavailable. Also, identify the critical data and IT assets like devices, applications, users, and servers for your business.
-
Determine What you Need to Protect Legally
While security and compliance are not the same, most organizations depend on the CISO for maintaining security compliance frameworks. Non-compliance is expensive and threatening for your business. Ensure that you design the cyber security plan with compliance frameworks and plan legal requirements.
-
Understand the Company’s Risk Appetite
Before creating a cyber security strategy, understand your organization’s risk assessments. Also, learn the amount of risk your organization can accept while pursuing strategic objectives. Risk appetites depend on the industry, the company’s financial strength, goals, and many more.
The cyber security plan for a startup won’t work for an established corporation. By learning the company’s risk appetite, ensure that you are not under-or-over protecting the business.
Step 2: Understand the Threat Landscape

Source
After learning what you have to protect, analyze and understand the threat landscape. Initially, understand the company’s environment for its operations. Know your potential customers, product or service you sell, disrupting the business benefits, etc. The questions help you learn about the general environment.
Also, learn about your competitors, threats they face, a security breach in the past, etc. The threats faced by competitors may also affect your business. Finally, learn about the type of threats you need to protect your business from and potential attackers. You can be well-prepared in defending the business by learning the answers to these questions.
Step 3: Create a Strategic Cyber Security Plan
-
Pick a Framework, Identify Current State of the Security Environment, and Build a Timeline
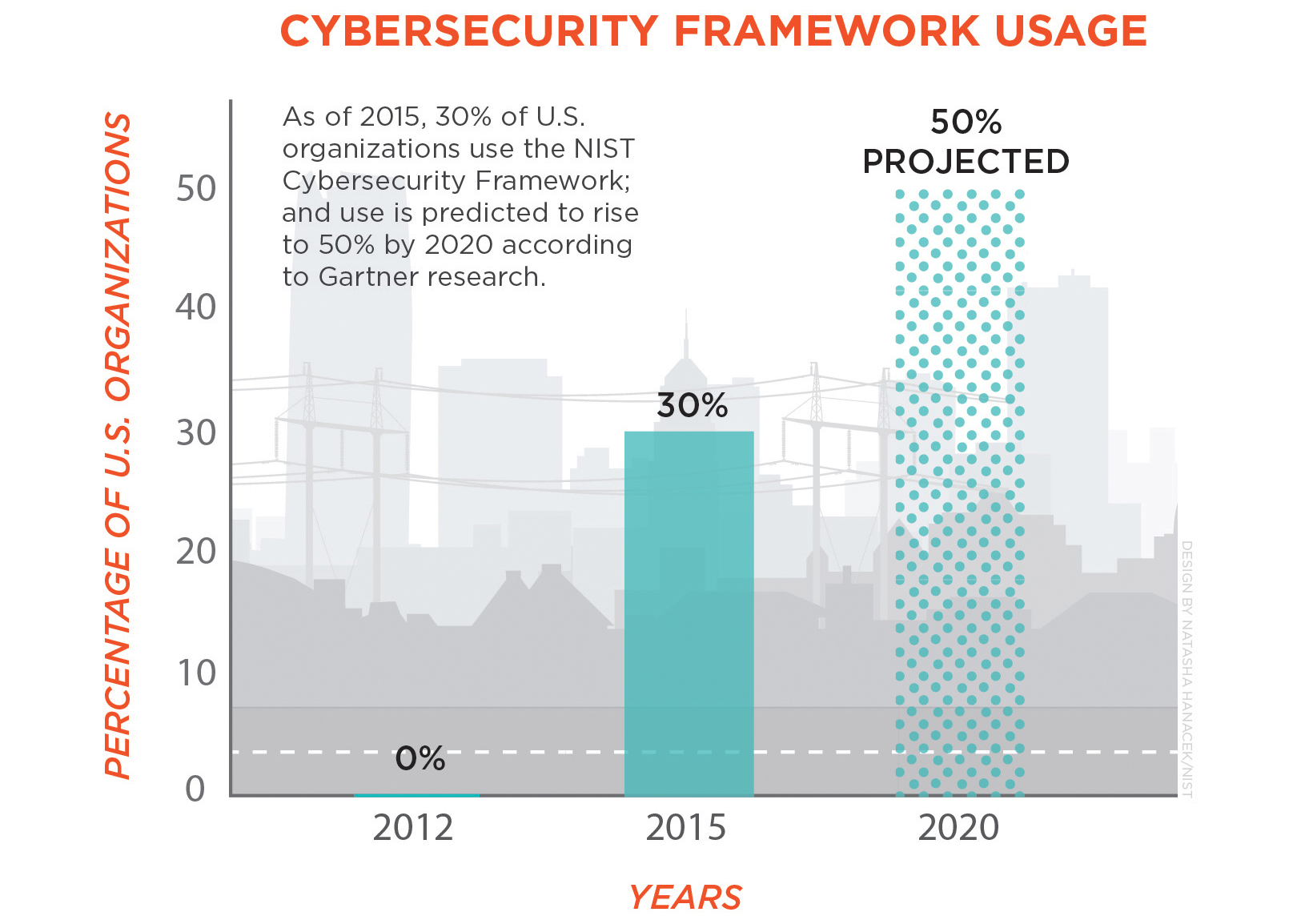
Source
Select a framework such as ISO, CIS Controls, and NIST to build a cyber security plan. It is essential to pick a framework to track progress effectively while prioritizing the critical steps. For example, the CIS Controls gives you a set of prioritized actions to save your organization and take these actions. In addition, it enables you to track progress to know what you have to do.
Once you know what you need to protect from the risk management point of view, evaluate current security measure effectiveness. Decide on a timeline, depending on the current security state. Things will change with time, needing occasional changes in the timeline. However, it is necessary to set a target timeline to get to your organization’s best risk level.
-
Evaluate Company’s Security Maturity Level
Evaluate the organization’s security maturity level using either outside consultants or in-house staff. Security maturity means a company’s adherence to security best processes and practices; measuring it allows you to identify areas for improvement.
Whether hiring a consultant or analyzing yourself, ensure that the process is repeatable. In this way, when you determine the security maturity in the coming years, you will have a benchmark for results comparison.
-
Evaluate the Technology Stack
Look at your current technology and identify tools you don’t use to their full benefit. Underutilized tools cost you time, money, and increase the attack surface. Then, find out the proper solutions to fulfil their original purposes. In addition, you can use the Cyber Defense Matrix to find security gaps. The Cyber Defense Matrix helps you understand what you need and which products solve your problems.
-
Identify Quick Wins and Foundational
While creating a cyber security strategy, identify the quick wins, foundational and high-risk items you must address initially. Then, identify future steps of the plan and prioritize actions. Quick wins are easy to fix things. Therefore, ensure that you have both quick wins and foundational tasks in the beginning.
Step 4: Evaluate Organization’s Ability to Execute a Cyber Security Plan
Finally, assess if your organization can get the necessary work done for security. Observe your current security and IT teams to understand their bandwidth and skill sets. If you don’t have the required resources, outsource some security work or augment your team members to execute the cyber security plan.
During this step, think about the future of your IT team or the business. Then, see if your IT team can handle any company-wide large-scale projects in the future.
Final Thoughts
The cybersecurity strategy development and implementation is an ongoing process and will face many challenges. Critically, it is important to monitor and reassess the organization’s cybersecurity maturity to measure the progress toward your objectives. The earlier you identify the falling area, the sooner you can report it to catch up.
Measuring progress includes tests and exercises, internal and external audits that simulate future events under various circumstances. Finally, rethink your cybersecurity strategy if a new threat arises. Agility in cyber security is very important. Don’t hesitate to update your plan with changes in security technologies and cyber threats. Or upgrade if your organization acquires new assets that require safeguarding.

by Anika D | Jan 17, 2022 | Business, Cybersecurity, General, Information Technology
The legal industry has transformed significantly over the years and will remain growing at a significant pace. As a result, various law firms worldwide are increasing their annual investments in voice technology. Voice technology gives a new face to the legal industry by providing several opportunities for market expansion, client experiences, or remote working. In addition, legal firms emphasize using voice technology to improve security, data storage, and other factors.
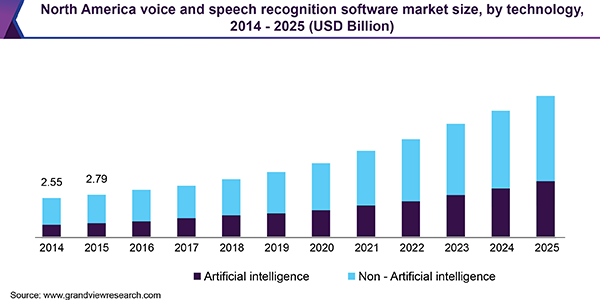
Source
Why Depend on Voice Technology?
Voice recognition helps to improve the productivity of corporate legal departments and law firms by supporting the tasks listed below:
- Reduce dependency on support staff
- Minimize document turnaround and streamline documentation efforts
- Dedicate extra time to understand the demands and problems of clients
- Lower transcription expenditure
- Focus on a business that can cross a lawyer’s desk.
You can easily achieve these tasks without changing existing information systems or processes. Voice recognition technology holds language modeling to determine and differentiate within millions of human expressions that produce a language. It uses statistical models for analyzing and interpreting incoming streams of utterances.
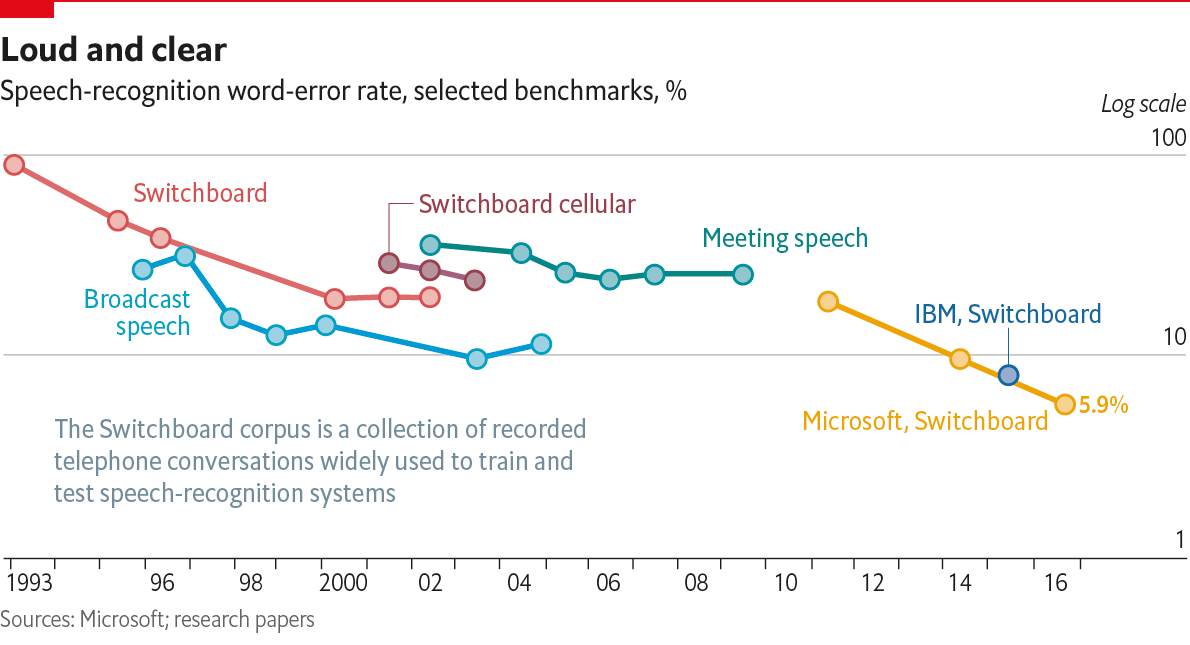
The latest advances in voice recognition significantly improve detection accuracy, performance, and usage ease. For example, Google’s Cloud Speech-to-Text can detect 120 languages and has attained 95 percent accuracy in the English language. These types of accomplishments are creating amazing discoveries in the legal domain.
Voice Technology Empowers the Legal Work
Each legal professional uses voice technology for several purposes, depending on their responsibilities and roles, workflow adjustments, and other needs. The primary beneficiaries of voice recognition in the legal industry are:
- Judges
- Attorneys or Lawyers
- Support Staff or Assistants
- Court Reporters
- Partners and Associates
- Law Students
- Transcriptionists
- Paralegals
- Legal Researchers
Voice technology in the legal domain includes the following applications:
-
Documents creation and management
Source
Law firms depend on paralegals, legal secretaries, or external transcriptionists to decipher the documents like legal briefs, client memos, contracts, and deposition summaries. It will hike the administrative charges of the law firms and extend the dictate – transcribe – review – edit cycle causing customer dissatisfaction.
A lawyer can dictate the document to their system instead of manually typing it using voice recognition software. This software transcribes the dictation automatically that you can review later to check accuracy.
-
Contract Review Automation
In most law firms, manual contract reviews consume considerable time and resources. AI-enabled word analytics offers the ability to analyze and review documents automatically with human-like knowledge. Application of Natural Language Processing (NLP) and data capture techniques allow us to identify facts, key sections, entities, or clauses from contracts and business documents. It also enables us to determine if the agreements meet the set criteria.
-
Audio and Text Summarization
A lawyer cannot replace voice recognition software’s impressive and fast processing power while surfing through large data. The voice recognition and analytics tool uses machine learning models to deliver precise summaries of lengthy documents. As a result, it can be useful for incorporating large information into a short report in legal work.
Bottom Line
Voice recognition APIs enable companies to look at call data surfacing details that empower legal professionals to care for their clients. Instead of randomly reviewing the small number of calls, lawyers use voice recognition softwares for proactive intervention.

by Anika D | Jan 12, 2022 | General
Face recognition is becoming the mainstream technology used in sectors starting from law enforcement to biometric security. In addition, many organizations started using it in light of the COVID-19 pandemic.
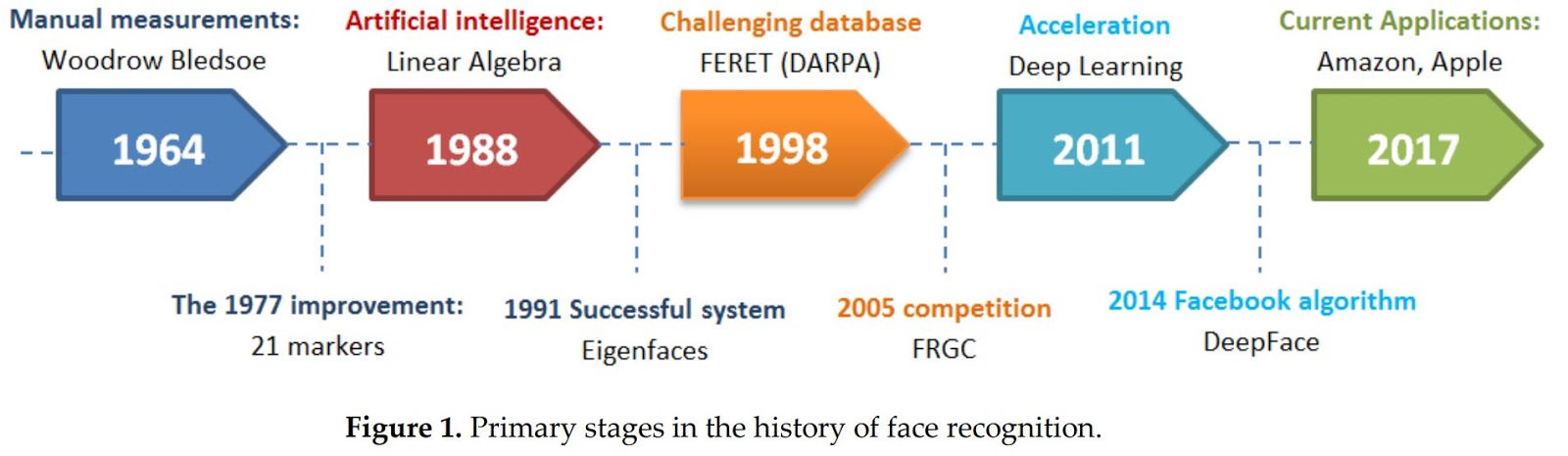
Source
Facial recognition technology has a great potential to reduce physical contact or personal interactions and enforce COVID safety rules. Moreover, various IT giants offer cloud-based services like Microsoft Azure’s Face, Amazon Web Services Rekognition, etc.
Amazon’s Rekognition is a service that goes beyond face matching by detecting activities and understanding the movement. The ability to identify people and understand everything happening in a scene expands the technology’s use and business value.
Future of Face Recognition Technology
Source
● Face Detection
Face detection technology performs the following essential tasks to obtain better performance of face-related applications:
- Determining facial regions in a picture against different backgrounds.
- Determining the face alignment, like size, position, and rotation.
With the development of various face-related applications, face detection technology has become important in recent years to detect faces under challenging situations.
● Face Alignment
Facial pose and expressions impact the accuracy of face recognition. Therefore, it is vital to align the shape and position of facial parts for accurate face recognition. So, it is necessary to have a robust
● Face Matching
Face matching technology extracts a vector feature from a face image to identify the pre-registration of the person in the photo. However, the conditions of registered and query images captured are not always the same.
Variations of illumination or posture and facial expressions constitute significant factors to match performance degradation. To solve this pose variation problem, you can use face normalization technology. It corrects the frontal face posture as well as the size and position of an image by using a 3D shape model.
Use Cases
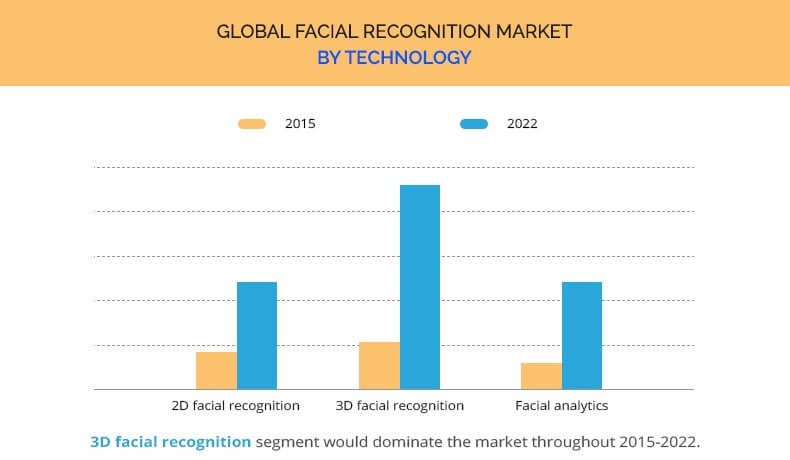
Source
The two critical applications for facial recognition technology are authentication and surveillance. Though both have a range of use cases, authentication has got acceptance by the public. It is convenient to outweigh the privacy implications.
The ease of unlocking Windows computers and smartphones with apps logging and authenticating transactions has made people comfortable with the technology. Meanwhile, it is also used in agreement with smart passports, speeding the immigration queues.
During COVID-19, most businesses apply facial recognition to build access management in the COVID-safe plan to return to work. It eliminates guest’s and staff’s requirement to check-in through communal touchscreen kiosks.
Face recognition technology can be integrated with self-service checkouts, supporting payments authorization or loyalty cards for completely touchfree transactions in the retail environment. In addition, various fraud detection applications in the financial sector are using this technology for two-factor authentication.
Also, some supermarkets are planning to encourage customers to ‘Just Walk Out’ with shopping bags by paying automatically. It is all thanks to artificial intelligence advances and facial recognition. The face recognition technology enables supermarkets to make completely checkout-less stores and minimal staff.
Conclusion
The future of face recognition technology is bright. It will indeed stay for a long time, so we should embrace its benefits. As seen above, various use cases show that facial recognition helps a lot. For example, it creates a safe environment, providing great security and enhancing customer experiences.
by Anika D | Jan 5, 2022 | General
Artificial Intelligence (AI) will be the touchstone that transforms many industries. This brings doubts regarding the role of women in AI. Its predecessor, Information Technology, suffered from the lesser participation of women in leadership positions. This is poised to change with women’s role as frontrunners in AI.
Let’s look at the top seven women leading the AI world.
Joy Buolamwini

Joy Buolamwini, an MIT graduate, is lauded for her groundbreaking research on algorithm bias. She single-handedly exposed the race and gender biases implicit in facial recognition algorithms.
In addition, this acknowledged the concession that facial recognition technology was not ready for public consumption yet. This did not stop the other commercial applications of artificial intelligence. Also, Buolamwini founded an organization called ‘Algorithmic Justice League.’
Rana el Kaliouby

Rana el Kaliouby has made it her life’s work to improve the emotional intelligence of AI. She has transformed the field of expression recognition research. Hence, the technology development is a subdivision of facial recognition, focused on emotion recognition. Kaliouby is ascribed to the pioneering field of Emotion AI.
Moreover, she is co-founder and CEO of Affectiva, an MIT spinout company that created machine learning algorithms that interpret human expressions and emotions. MIT recently published a study on a new machine learning model that understands object relationships.
Daphne Koller

Koller has been a professor at Stanford since 1995, specializing in Machine Learning. She and her colleague, Andrew Ng, were the founders of the edu-tech business behemoth ‘Coursera.’ Most recently, Koller is the Founder-CEO of Insitro. It’s a firm that uses machine learning to revolutionize pharmacological medication research.
Anna Patterson

Anna Patterson is the founder and Managing Partner of Gradient Ventures. Her remarkable career delved into designing and delivering artificial intelligence to startups and major tech companies. Also, she started her career with Google and was promoted to the company’s VP of Engineering for many years.
Daniela Rus

She is the first female head of MIT’s Computer Science and Artificial Intelligence Lab (CSAIL). This is one of the most prestigious and prominent labs in the world. Her breakthrough research shows its impact on networked collaborative robots, self-configurable robots, and soft robots. In addition, she believes that a robot is a tool and can be extremely beneficial. Moreover, her efforts have led to artificial intelligence used everywhere.
Claire Delauney

Claire Delaunay has held leadership roles in many of Silicon Valley’s renowned firms. Her resume spans work with SRI, Google, Uber, and NVIDIA. Also, she is the co-founder of Otto. In addition, she is currently working on a platform that allows autonomous machines to be deployed at scale.
Fei Fei Li

She founded and managed the ImageNet initiative. It’s a repository of millions of tagged photos that have altered the course of AI. in addition, it formed the basis of deep learning. Moreover, reports say that Geoff Hinton and his colleagues used their neural network-based model AI trained on ImageNet.
Finally, artificial intelligence is changing the way you work. Moreover, the potential for what is possible. Also, it’s an avenue for women-led growth and development. These extraordinary women are trailblazing the way to the future.

by Anika D | Dec 29, 2021 | Blockchain, Business
An increasing number of women are claiming the space around blockchain technology, NFTs and cryptocurrency. This promises to be an exciting prospect as technology and finance are male-dominated fields.
As Bitcoin has reached record highs in recent years, one cannot help but note that the younger generations seem more invested. This also presents a chance for women to stop being underrepresented in digital spaces.
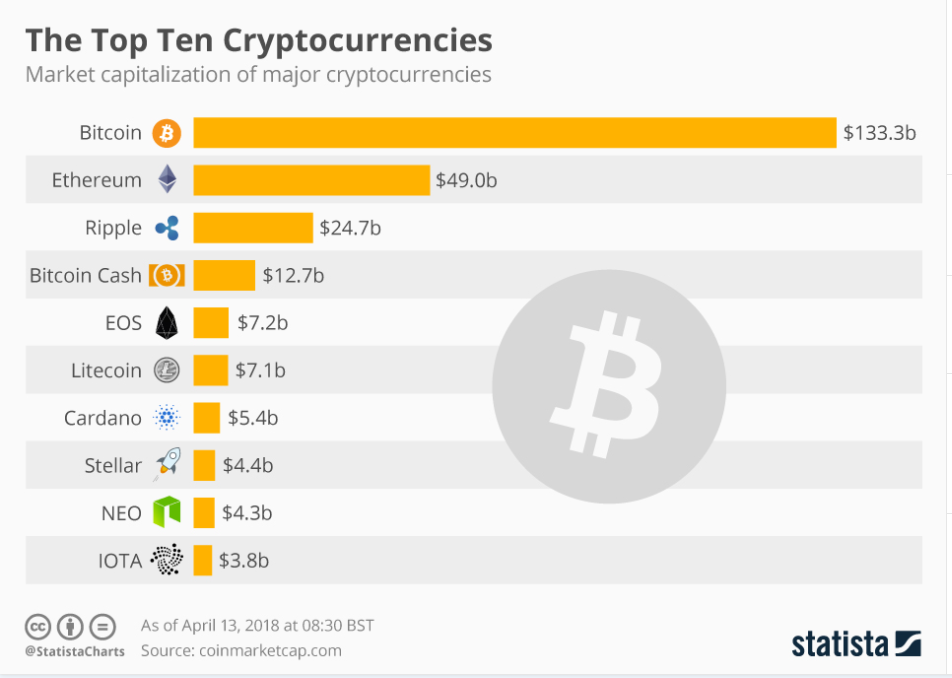
Source
This does not have to stand when you consider financial avenues provided by Bitcoin as an investment. Using blockchain technology and cryptocurrency can address issues ranging from digital education for girls in under-developed countries to wealth gap inequalities.
What are Blockchain Technology, NFTs, and Cryptocurrency?
Blockchain is a public digital ledger that records financial transactions in ‘blocks.’ Each block is a time-stamped encrypted file with data on the previous trade. With every additional transaction, they form a chain of blocks. The best use for blockchain technology is as an anti-corruption tool.
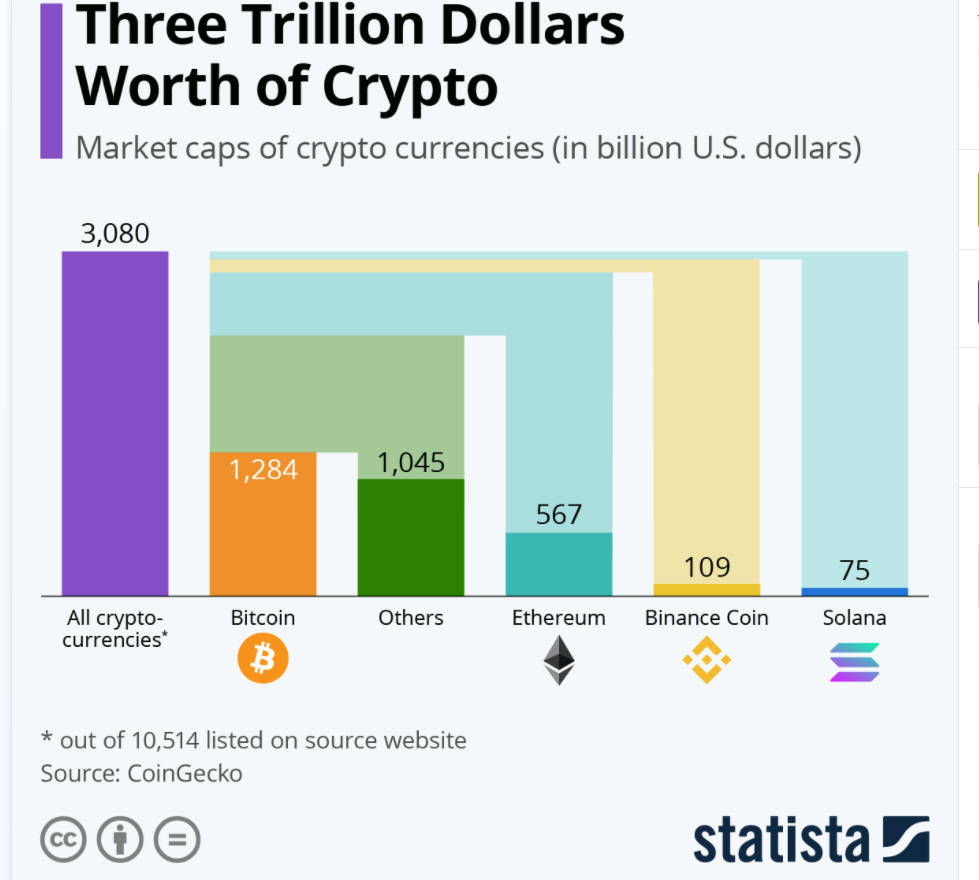
Source
Cryptocurrencies are the main components of digital payments systems. It enables peers to make and receive payments. The decentralization element is that banks don’t keep records of these transactions. It gets recorded in a public ledger.
Non-Fungible Tokens (NFTs) are unique non-interchangeable data stored in a block. It is proof that you have ownership of a digital or physical asset. Users can copyright the investment, buy or sell them.
This technology is revolutionizing the way you can keep assets and presents a unique opportunity for vulnerable populations to invest or sell their art. Thanks to decentralization, it provides a fairer, inclusive, and more resilient path to financial security for women.
Creating Space For Women In The Cryptocurrency World
More than two-thirds of U.S. cryptocurrency investors are men. About 60% are white, and according to a recent survey by CNBC and Acorn, the gender gap is wider than in other financial investments such as stocks, bonds, and mutual funds.
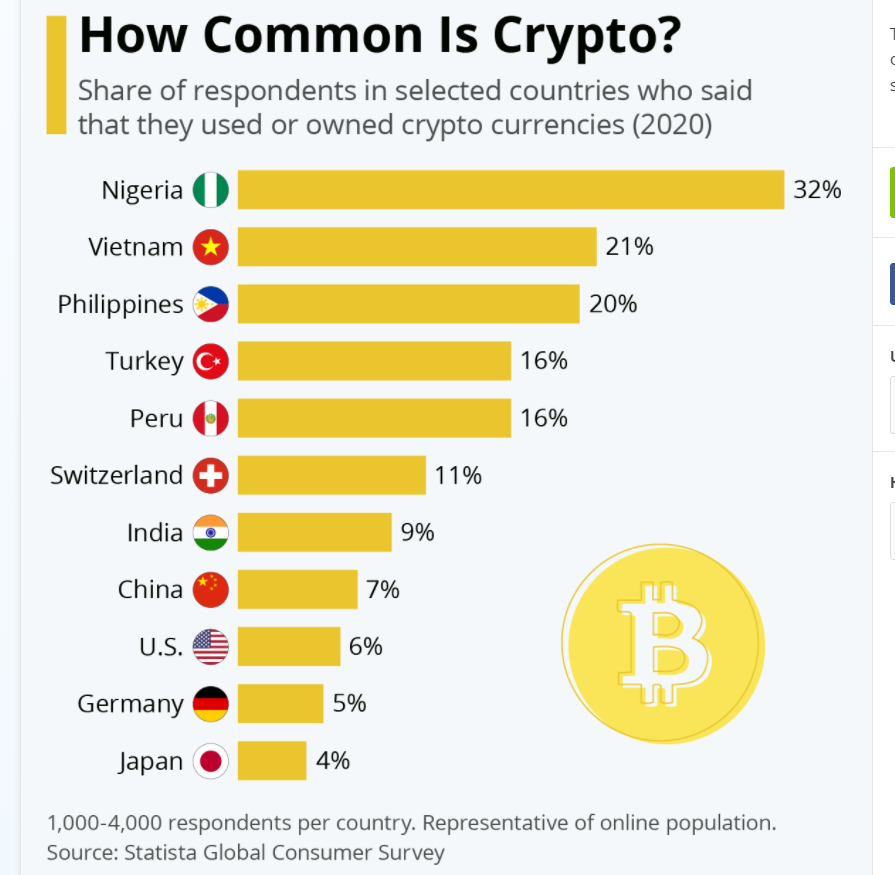
Source
Cryptocurrencies and NFTs provide a once-in-a-lifetime opportunity to bridge the gender gap in a newly expanding horizon. In addition, with Cryptocurrency going mainstream, it’s crucial to have the input of women and diverse actors to create a better future for crypto and NFTs.
When you consider the long-term implications of blockchain technology, you need to glean if cryptocurrency is a good investment for your portfolio. If not, an investment in NFTs might be on the cards.
If so, then women may lead the cryptocurrency community. A recent study found that female investors tend to be more analytical and carry thorough risk assessments with their investments. This is only beneficial in the volatile markets provided by cryptocurrency.
Blockchain technology and cryptocurrency thrive in communities, which benefit from women’s skillset in helping them grow and develop. Moreover, it creates a forum for women to take the initiative and lead the way. This will address the skewed balance of the blockchain ecosystem. In addition, the impact of the blockchain will ripple out to other industries, which will benefit from having women at the helm.


























